What is a Brute Force Attack
A brute force attack is a type of cyberattack where an attacker systematically tries every possible combination of characters, numbers, or symbols in an attempt to guess a password, encryption key, or other secret information. The attacker uses automated tools to quickly run through all possible combinations until the correct one is found. This method is time-consuming and may take a long time to succeed, but it can be effective against weak passwords or encryption keys. To protect against brute force attacks, it is recommended to use strong, unique passwords and to implement proper security measures such as rate limiting, two-factor authentication, and encryption.
Types of Brute Force Attacks
There are several types of brute force attacks, including:
Dictionary Attack: An attacker tries to guess a password by using a pre-existing list of words or commonly used passwords.
Hybrid Attack: A combination of dictionary and brute force methods, where the attacker tries to guess the password by combining words from a dictionary with numbers and symbols.
Rainbow Table Attack: The attacker uses pre-computed tables of hashes to crack encrypted passwords more quickly than with a traditional brute force attack.
Mask Attack: The attacker knows some information about the target password, such as its length, and uses this information to reduce the number of possibilities to be tested.
Reverse Brute Force Attack: The attacker already has the encrypted password and is trying to determine the original plaintext password.
Regardless of the method used, brute force attacks can be prevented by using strong, unique passwords, implementing proper security measures, and staying up-to-date with software and security updates.
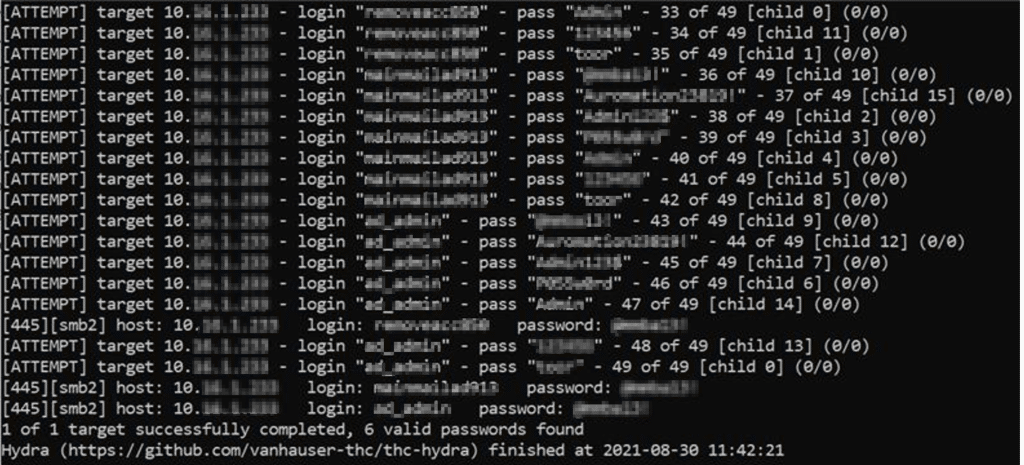
Hydra and Other Popular Brute Force Attack Tools
Hydra is a popular, open-source tool used for conducting brute force attacks against various network protocols and services, such as FTP, HTTP, SMTP, and Telnet. Some of the other popular brute force attack tools include:
John the Ripper: A popular password cracking tool that can be used for cracking passwords for various services, including FTP, Telnet, and SMTP.
Ncrack: A high-speed network authentication cracking tool that supports a variety of protocols, including SSH, Telnet, and RDP.
Aircrack-ng: A wireless network security tool that can be used for cracking WEP and WPA encryption keys.
THC-Hydra: A tool that specializes in cracking remote authentication services, such as FTP, HTTP, SMTP, and Telnet.
It is important to note that the use of these tools is illegal in many countries, and their use is only recommended for penetration testing and ethical hacking purposes. Additionally, it is essential to always use these tools with caution and follow best security practices to avoid causing harm to systems and networks.
Other top brute force tools are
Here are some of the other top brute force tools:
Cain and Abel: A Windows-based tool that can be used to perform various security attacks, including brute force password cracking.
Ophcrack: A free Windows password cracker that uses rainbow tables to crack passwords.
Brutus: A free, remote online password cracker for Windows, Linux, and other operating systems.
L0phtCrack: A commercial password cracking tool for Windows that can be used to audit password security and perform password recovery.
Metasploit: An open-source framework for developing, testing, and executing exploits and payloads, including brute force attacks.
SQLmap: An open-source tool for automating the process of detecting and exploiting SQL injection vulnerabilities, which can also be used for brute force attacks against databases.
Patator: A multi-threaded tool for brute forcing various types of authentication systems and protocols, including HTTP, FTP, SSH, Telnet, and others.
Fuzzing: A technique used for finding vulnerabilities in software by bombarding it with unexpected or random data inputs, which can be used for brute force attacks in some cases.
Heading TitleWeak Passwords that Enable Brute Force Attacks
Weak passwords make it easier for attackers to conduct brute force attacks and successfully gain access to sensitive information. Some of the most common types of weak passwords include:
Short Passwords: Passwords that are too short (less than 8 characters) are easily cracked using brute force techniques.
Dictionary Words: Passwords that are based on dictionary words, such as “password”, “1234”, or “admin” are easily guessed and should be avoided.
Sequential Numbers or Letters: Passwords that are based on simple sequences of numbers or letters, such as “abc123” or “qwerty”, are also easily cracked.
Personal Information: Passwords that include personal information, such as birthdays, names, or addresses, are vulnerable to attacks.
Reused Passwords: Using the same password for multiple accounts makes it easier for attackers to gain access to sensitive information if one password is cracked.
It is recommended to use strong, unique passwords that include a mix of uppercase and lowercase letters, numbers, and symbols. Additionally, using password managers and enabling two-factor authentication can help protect against brute force attacks.
How to Prevent Brute Force Password Hacking
Here are some steps that can be taken to prevent brute force password hacking:
Use Strong Passwords: Use strong, unique passwords that include a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using personal information, dictionary words, or simple sequences as passwords.
Enable Two-Factor Authentication (2FA): Two-factor authentication adds an extra layer of security to your accounts by requiring a second form of authentication in addition to a password, such as a code sent to your phone.
Use a Password Manager: A password manager can help you generate and store strong, unique passwords for all of your accounts.
Implement Rate Limiting: Rate limiting helps prevent brute force attacks by limiting the number of login attempts an IP address can make in a specific time period.
Monitor Login Attempts: Regularly monitoring login attempts can help you identify and respond to potential brute force attacks.
Keep Software and Security Up-to-date: Regularly updating software and security measures can help prevent known vulnerabilities from being exploited by attackers.
Encrypt Sensitive Data: Encrypting sensitive data helps protect it from being accessed by unauthorized individuals, even if they are able to successfully guess a password.
By taking these steps and following best security practices, you can help protect against brute force password hacking and keep sensitive information secure.
Brute Force Attack Prevention with Imperva
Imperva is a cybersecurity company that offers a range of solutions for preventing brute force attacks. Some of the features and capabilities of Imperva’s brute force attack prevention solution include:
IP Reputation: Imperva uses a global threat intelligence network to identify and block malicious IP addresses that are known to be associated with brute force attacks.
Account Lockout: Imperva can automatically lock out accounts that are the target of brute force attacks, making it more difficult for attackers to gain access to sensitive information.
Rate Limiting: Imperva can limit the number of login attempts that can be made from a single IP address, reducing the risk of a successful brute force attack.
Real-Time Alerts: Imperva provides real-time alerts and notifications when a potential brute force attack is detected, allowing you to quickly respond and take action.
Custom Rules: Imperva allows you to create custom rules and policies for your specific security needs, allowing you to tailor your protection against brute force attacks.
By using Imperva’s brute force attack prevention solution, organizations can proactively protect against these types of attacks and help secure sensitive information. Additionally, Imperva offers a comprehensive suite of cybersecurity solutions, including web application firewall (WAF) and DDoS protection, that can help further enhance security.
