Users of Mirth Connect, NextGen Healthcare’s open-source data integration platform, are being urged to update to the latest version after the discovery of an unpatched remote code execution vulnerability.
Tracked as CVE-2023-43208, the vulnerability has been addressed in version 4.4.1, released on October 6, 2023.
“This is an easily exploitable, unauthenticated remote code execution vulnerability,” Naveen Sunkavally of Horizon3.ai said in a report on Wednesday. “Attackers would likely exploit this vulnerability to gain initial access or compromise sensitive health care data.”
Called the “Swiss Army Knife of healthcare integration”, Mirth Connect is a cross-platform interface engine used in the healthcare industry to communicate and exchange data between disparate systems in a standardized manner.
Additional technical details about the flaw have been withheld in light of the fact that the 2015/2016 Mirth Connect versions have been found to be vulnerable to this issue.
It’s worth noting that CVE-2023-43208 is a patch bypass for CVE-2023-37679 (CVSS score: 9.8), a critical remote command execution (RCE) vulnerability in the software that allows attackers to execute arbitrary commands on the hosting server.
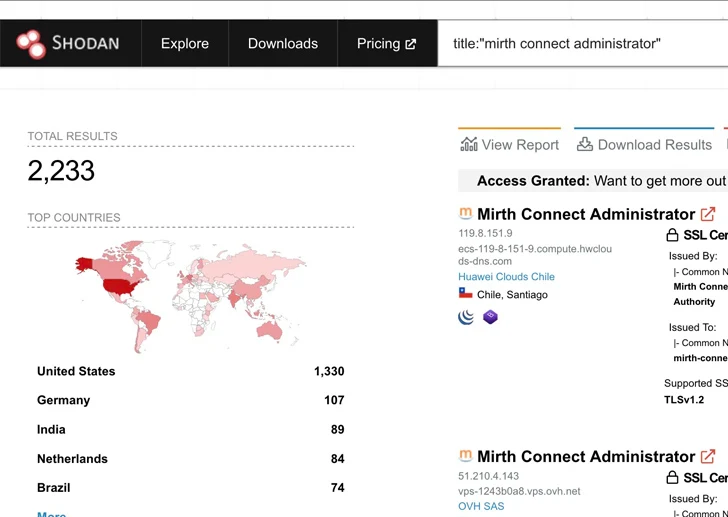
While CVE-2023-37679 was described by its maintainers as only affecting servers running Java 8, Horizon3.ai’s analysis found that all instances of Mirth Connect, regardless of the Java version, were susceptible to the problem.
Given the ease with which the vulnerability can be trivially abused, coupled with the fact that the exploitation methods are well known, it’s recommended to update Mirth Connect, particularly that are publicly accessible over the internet, to version 4.4.1 as soon as possible to mitigate potential threats.
