A government entity in Guyana has been targeted as part of a cyber espionage campaign dubbed Operation Jacana.
The activity, which was detected by ESET in February 2023, involved a spear-phishing attack that led to the deployment of an as-yet-unspecified exploit written in C++, called DinodasRAT.
The Slovak cybersecurity firm said it could not link the intrusion to any known threat actor or group, but could attribute it with moderate confidence to a China-Nexus rival due to the use of PlugX (aka KorPlug), which Chinese remote access trojan is hacking team.
“This campaign was targeted, as the threat actors crafted their emails specifically to lure in their chosen victim organization,” ESET said in a report.
“After successfully compromising an initial but limited set of machines with DinodasRAT, the operators moved on and breached the target’s internal network, where they again deployed this backdoor.”
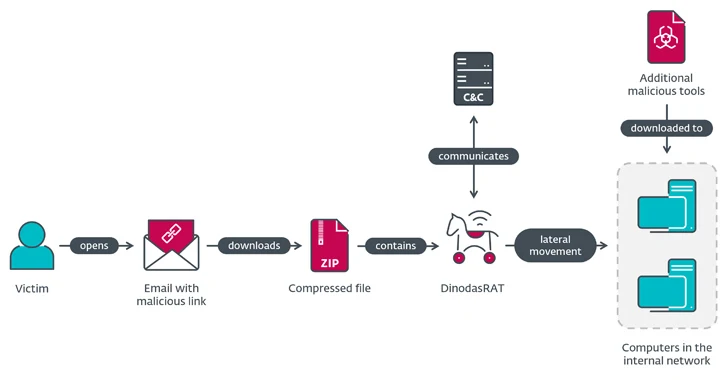
The infection sequence began with a phishing email that contained an unknown link with subject lines referencing a purported news report about a Guyanese fugitive in Vietnam.
If the recipient clicks the link, a zip archive file from the domain fta.moit.gov[.]vn is downloaded, indicating the Vietnamese government website’s agreement to host the payload.
Embedded within the zip archive is an executable that launches the DinodasRAT malware to collect sensitive information from the victim’s computer.
In addition to encrypting information sent to a command-and-control (C2) server using DinodasRAT, the Tiny Encryption Algorithm (TEA), the system can extract metadata, files, manipulate Windows registry keys, and execute commands.
Also deployed are tools for lateral movement, KorPlug, and the SoftEther VPN client, the latter of which has been used by another China-affiliated cluster tracked by Microsoft as Flax Typhoon.
“The attackers used a combination of previously unknown tools, such as DinodasRAT, and more traditional backdoors, such as KorPlug,” said ESET researcher Fernando Tavella.
“Based on the spear-phishing emails used to gain initial access to the victim’s network, operators are tracking the geopolitical activities of their victims to increase the chances of success of their operations.”