The US Federal Bureau of Investigation (FBI) is warning about cyber crooks posing as legitimate non-fungible token (NFT) developers to steal cryptocurrencies and other digital assets from unknown users.
In these fraudulent schemes, criminals either obtain direct access to NFT developer social media accounts or create look-alike accounts to promote “exclusive” new NFT releases, often employing misleading advertising campaigns that create a sense of urgency to pull them off.
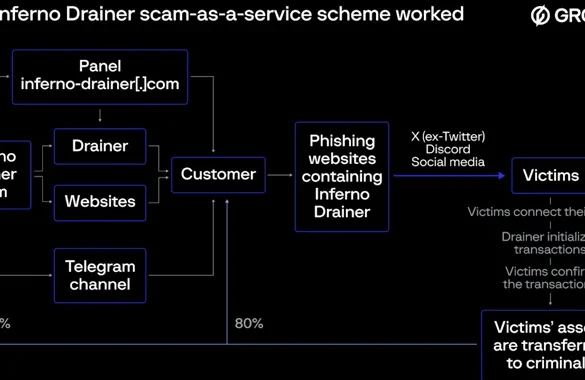
“The links provided in these announcements are phishing links that direct victims to a fake website that appears to be a legitimate extension of a particular NFT project,” the FBI said in an advisory last week.
Replication websites solicit potential targets to connect their cryptocurrency wallets and purchase NFTs, only for the threat actors to transfer the funds and NFTs to wallets they control.
“Content stolen from victims’ wallets is often processed through a series of cryptocurrency mixers and exchanges to obscure the path and final destination of the stolen NFTs,” the agency said.
To reduce the risks posed by such scams, it is recommended that users perform due diligence and review social media accounts and websites to verify their legitimacy.
The development comes nearly five months after the FBI warned of a rise in fraudulent cryptocurrency investment schemes called Pig Slaughter (or Sha Zhu Pan) that would result in losses of $2 billion in 2022.
This includes a category called CryptoRom in which criminals use fictitious identities on dating apps and social media platforms to develop romantic relationships and build trust with victims before introducing them to the idea of cryptocurrency trading.
Operators have been known to engage in initial conversation within the app with which they made initial contact with the target. Soon after, the chats are moved to private messaging apps such as Telegram or WhatsApp, where they encourage them to use fraudulent crypto websites or apps and make substantial investments.
“Criminals coach victims through the investment process, showing them fake profits and encouraging victims to invest more,” the FBI said. “When victims try to withdraw their money, they are told that they must pay a fee or tax. Victims cannot get their money back, even if they pay the fee or tax imposed.”
The romance-centered social engineering attacks have also gotten a facelift in recent months, with Sophos identifying apps on the Apple App Store and Google Play Store that make use of generative AI features to lend more credibility to conversations with the victims on messaging apps like WhatsApp.
“These apps are able to get past review by Apple and Google by remotely modifying the content associated with the app after it has been approved and published to the store,” the cyber security company said.
“By simply changing a pointer in the remote code, an app can be switched from a benign interface to a fraudulent interface without further review by Apple or Google, unless a complaint has been filed.”