New findings suggest that malicious actors can take advantage of stealthy malware detection evasion techniques and bypass endpoint protection solutions by manipulating the Windows Container Isolation Framework.
The findings were presented by Deep Instinct security researcher Daniel Avinoam at the DEF CON security conference held earlier this month.
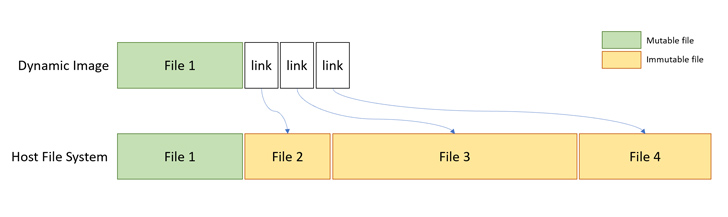
Microsoft’s container architecture (and by extension, Windows Sandbox) uses a dynamically generated image to isolate the file system from each container to the host, as well as to avoid duplication of system files.
It is an “operating system image that contains clean copies of files that may change, but links to files that may not change that are in the Windows image that already exists on the host,” thereby creating a composite image for the complete OS size decreases.
“The result are images that contain ‘ghost files’ that store no real data but point to a different volume on the system,” Avinoam said in a report shared. “That’s when this idea came to my mind – what if we could use this redirection mechanism to obfuscate our file system operations and obfuscate security products?”
This is where the Windows Container Isolation FS (wcifs.sys) minifilter driver comes in handy. The main purpose of the driver is to take care of the separation of file systems between Windows containers and their hosts.
The driver handles the redirection of ghost files by parsing their attached reparse points and the corresponding reparse tag that uniquely identifies the owner, i.e., the implementer of the file system filter driver that performs additional filter-defined actions on the file during I/O operations.
According to Microsoft, two such reparse tag data structures used by the Windows Container Isolation Filter are IO_REPARSE_TAG_WCI_1 and IO_REPARSE_TAG_WCI_LINK_1.
In short, the idea is to run the current process inside a fabricated container and leverage the minifilter driver to handle I/O requests so that it can create, read, write files on the file system without alerting the security software and can remove.
It is worth pointing out at this stage that a minifilter connects indirectly to the file system stack by registering with the filter manager for the I/O operations it has chosen to filter. Each minifilter is assigned an “integer” height value specified by Microsoft based on filter requirements and the load order group.
The wcifs.sys driver operates on an elevation range of 180000–189999 (specifically 189900), while antivirus filters, including third-party ones, operate on an elevation range of 320000–329999. As a result, various file operations can be performed without triggering their callbacks.
“Because we can override files using the IO_REPARSE_TAG_WCI_1 reparse tag without antivirus drivers detecting them, the algorithms that detect them will not get the full picture and thus will not trigger,” Avinoam explained.
As noted, the attack requires administrative permission to communicate with the wcifs.sys driver and cannot be used to override files on the host system.
The revelation came after the cybersecurity company demonstrated a secret technique called NoFilter that abuses the Windows Filtering Platform (WFP) to escalate a user’s privileges to system privileges and potentially execute malicious code.
The attacks allow the use of WFP to duplicate access tokens for another process, trigger an IPSec connection and leverage the Print Spooler service to insert a SYSTEM token into the table, and make it possible to obtain the token of another user logged into the compromised system for lateral movement.
