Tracked as CVE-2023-38646, this issue affects open-source versions prior to 0.46.6.1 and Metabase Enterprise versions prior to 1.46.6.1.
“An unauthenticated attacker could run arbitrary commands on the server on which you are running Metabase with the same privileges as the Metabase server,” Metabase said in an advisory issued last week.
This issue has also been addressed in the following older versions –
- 0.45.4.1 and 1.45.4.1
- 0.44.7.1 and 1.44.7.1, and
- 0.43.7.2 and 1.43.7.2
While there is no evidence that the issue has been exploited in the wild, data gathered by the Shadowserver Foundation shows that 5,488 out of the total 6,936 Metabase instances are vulnerable as of July 26, 2023. A majority of the instances are located in the U.S., India, Germany, France, the U.K., Brazil, and Australia.
Assetnote, which claimed it discovered the bug and reported it to Metabase, said the vulnerability is caused by a JDBC connection issue in the API endpoint “/api/setup/validate”, which could allow a malicious actor to obtain a reverse shell on the system. A specially crafted request that takes advantage of an SQL injection flaw in the H2 database driver.
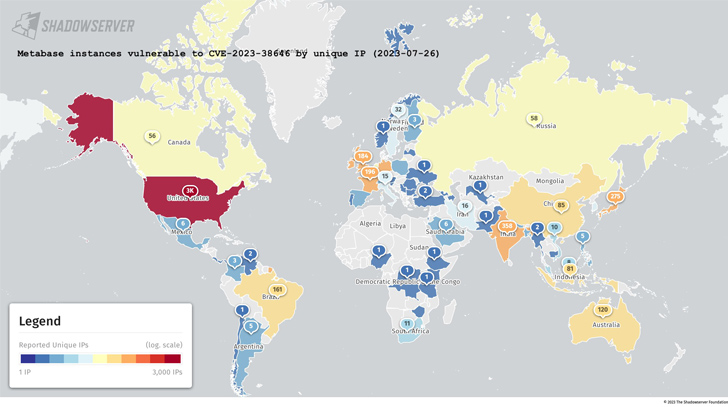
Users who cannot apply the patch immediately are advised to block requests to the /api/setup endpoint, isolate the metabase instance from their production network, and monitor suspicious requests on the relevant endpoint.



