Threat actors are using an open-source rootkit called Reptile to target Linux systems in South Korea.
AhnLabs Security Emergency Response Center (ASEC) said in a report published this week, “Unlike other rootkit malware, which typically only offer the ability to disguise, Reptile goes a step further by offering a reverse shell, allowing allowing threat actors to easily take control of the system.”
“Port knocking is a method where malware opens a specific port on an infected system and goes on standby. When the threat actor sends a magic packet to the system, the received packet is used to establish a connection with the C&C server is used as the basis for.
A rootkit is a malicious software program designed to provide privileged, root-level access to a machine while disguising its appearance. At least four different missions have taken advantage of Reptile since 2022.
The first use of a rootkit was reported by Trend Micro in May 2022 in connection with an intrusion set tracked as Earth Barbaroka (aka GamblingPuppet), which used malware to hide connections and processes related to cross-platform Python Trojans found to be in use. In attacks on gambling sites in China, it is known as the Pupy RAT.
Then in March 2023, Google-owned Mandiant detailed a set of attacks carried out by a suspected China-linked threat actor named UNC3886, which included a number of custom implants as well as zero-into Fortinet devices to deploy Reptile. The loopholes of the day were planned.
In the same month, ExaTrack disclosed the use of Linux malware by a Chinese hacking group called melofée, which is based on Reptile. Ultimately, in June 2023, a cryptojacking operation discovered by Microsoft used a shell script backdoor to download Reptile to obfuscate its child processes, files, or their contents.
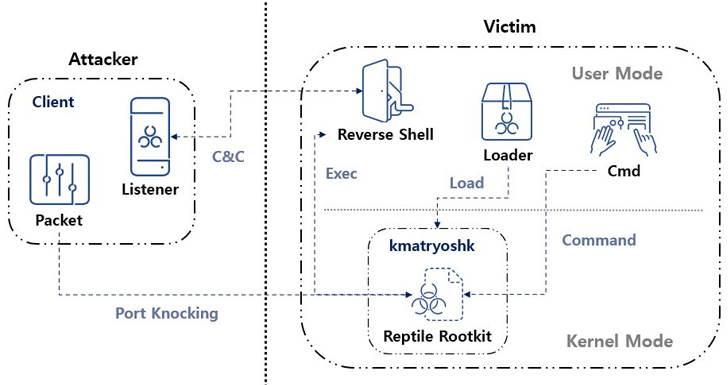
A closer examination of Reptile reveals the use of a loader, which uses a tool called kmatryoshka to decrypt and load the rootkit’s kernel module into memory, after which it opens a specific port and awaits for the attacker to transmit a magic packet to the host over protocols such as TCP, UDP, or ICMP.
ASEC said, “The data received via magic packet includes the C&C server address.” “Based on this, a reverse shell connects to the C&C server.”
It is worth noting that the use of magic packets to activate malicious activity has previously been seen in another rootkit called Syslogk, which was documented by Avast last year.
The South Korean cyber security firm said it also detected an attack case in the country that involved the use of Reptile, which bears some tactical similarities with melofée.
ASEC said, “Reptile is a Linux kernel mode rootkit malware that provides a hidden access to files, directories, processes, and network communications.” “However, Reptile itself also provides a reverse shell, making systems with Reptile installed more susceptible to hijacking by threat actors.”