In a new report shared with The Hacker, Sysdig security researcher Alessandro Brucato said, “Cloud environments are still their primary target, but the tools and techniques used are more flexible and covert command and control architectures as well.” There are new security technologies.” are adapted to circumvent the measures.”
SCARLETEEL was first exposed by a cybersecurity company in February 2023, detailing a sophisticated attack series that culminated in the theft of proprietary data from the AWS infrastructure and illegal access to the resources of the compromised systems. Cryptocurrency miners were deployed to make profits.
A follow-up analysis by Cado Security uncovered possible links to a prolific cryptojacking group called TeamTNT, although Sysdigg told The Hacker News that “it could be someone copying their methodology and attack patterns.”
Latest Activity Threats to go behind AWS accounts by exploiting vulnerable public-facing web applications to gain persistence, steal intellectual property, and potentially generate $4,000 a day revenue using crypto miners Continues the wale actor trend.
“The actor discovered and exploited a flaw in AWS policy, which allowed them to elevate administrator access privileges and gain control over the account, enabling them to do whatever they wanted,” Brucato explained.
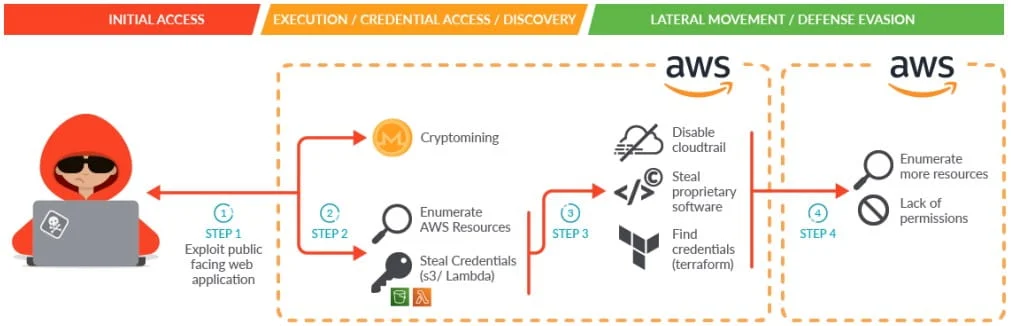
It all starts with an exploit by the adversary of JupyterLab notebook containers deployed in a Kubernetes cluster, leveraging the initial premise to gather AWS credentials to perform reconnaissance of the target network and gain deep access to the victim’s environment.
This is followed by the installation of AWS command line tools and an exploit framework called Pacu for subsequent exploitation. The attack is also known to use various shell scripts to retrieve AWS credentials, some of which target AWS Fargate Compute Engine instances.
“The attacker was observed using an AWS client that is compatible with the S3 protocol to connect to Russian systems,” Brucato said. SCARLETEEL actors used covert techniques to ensure that data intrusion events were not captured in CloudTrail logs.
Some other steps taken by the attacker include the use of a Kubernetes penetration testing tool called Pirates and a DDoS botnet malware called Pandora to exploit the container orchestration system, indicating further efforts from the actor to monetize the infected hosts.
“SCARLETEEL actors continue to operate against targets in the cloud, including AWS and Kubernetes,” Brucato said. “Their preferred method of entry is the exploitation of open compute services and vulnerable applications. There is a continued focus on monetary gain through crypto mining, but […] intellectual property is still a priority.”
