It has emerged that the firewall and distributed denial-of-service (DDoS) attack prevention mechanisms in Cloudflare can be circumvented by exploiting gaps in cross-tenant security controls, defeating the purpose of these security measures.
“Attackers could use their own Cloudflare accounts to abuse the per-design trust-relationship between Cloudflare and customers’ websites, rendering the security mechanisms ineffective,” Certtitude researcher Stefan Proksch said in a report published last week.
The problem, according to the Austrian consulting firm, is a result of the shared infrastructure available to all tenants within Cloudflare, regardless of whether they are legitimate or otherwise, which would have made it easier for malicious actors to abuse the inherent trust associated with the service and defeat guardrails.
The first issue arises from choosing a shared Cloudflare certificate to authenticate HTTP(S) requests between the service’s reverse proxy and the client’s origin server as part of a feature called Authenticated Origin Pulls.
As the name suggests, Authenticated Origin Pull ensures that requests sent to the origin server to fetch content when it is not available in the cache come from Cloudflare, and not from a threat actor.
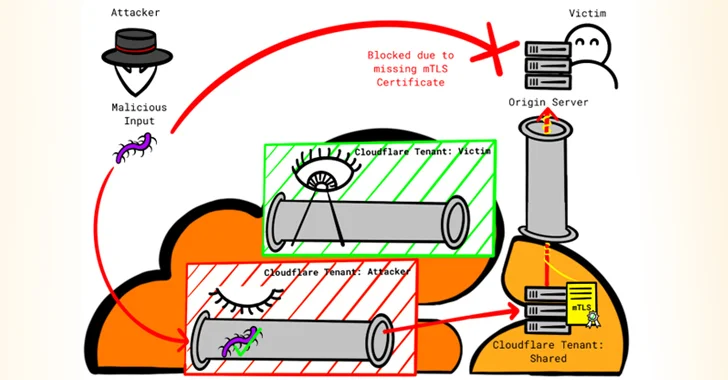
One consequence of such a setup is that an attacker with a Cloudflare account can send their malicious payload through the platform by taking advantage of the fact that all connections originating from Cloudflare are allowed, even if the tenant initiating the connection is nefarious.
“An attacker can set up a custom domain with Cloudflare and point a DNS A record to the victim’s IP address,” Proksch explained.
“The attacker then disables all security features for that custom domain in their tenant and tunnels their attack through the Cloudflare infrastructure. This approach allows attackers to bypass security features set by the victim.”
The second problem involves the abuse of allowing Cloudflare IP addresses – which prevents the origin server from receiving traffic from individual visitor IP addresses and limits it to Cloudflare IP addresses – to broadcast rogue input and target other users on the platform.
Following the alleged disclosure on March 16, 2023, Cloudflare considered the findings informative, and added a new warning to its documentation.
Cloudflare now clearly says, “Note that the certificate that Cloudflare provides you to establish an authenticated origin bridge is not specific to your account, it merely guarantees that the request is coming from the Cloudflare network.”
“For more stringent security, you should install a certified origin bridge with your own certificate and consider other security measures for your origin.”
“The ‘AllowList Cloudflare IP Address’ mechanism should be treated as defense in depth, and should not be the only mechanism to protect the origin server,” Proksch said. “The ‘Authenticated Origin Pulls’ mechanism should be configured with custom certificates instead of Cloudflare certificates.”
Certitude also previously revealed that it was possible for attackers to take advantage of “dangling” DNS records to hijack subdomains belonging to more than 1,000 organizations spanning governments, media outlets, political parties and universities, and potentially distribute malware, It is possible to use them for disinformation campaigns and phishing attacks.
Security researcher Florian Schweitzer said, “In most cases, subdomain hijacking can be effectively prevented by cloud services through domain ownership verification and identifiers already used for registration cannot be immediately released. “
The disclosures arrive as Akamai revealed that adversaries are increasingly leveraging dynamically seeded domain generation algorithms (DGA) to avoid detection and complicate analysis, effectively extending the lifespan of command-and-control (C2) communication channels.
Security researchers Connor Faulkner and Stijn Tilborghs said, “Knowing which DGA domains will be active tomorrow allows us to proactively place these domains on our blocklist to protect end users from botnets.”
“Unfortunately, this scenario is not possible with unpredictable seeds like Google Trends, temperature or foreign exchange rates. Even if we have the source code of the family, we are not able to accurately predict the DGA domain names that will be generated in the future.”
Back in August, a group of academics from the University of California, Irvine and Tsinghua University demonstrated a DNS poisoning attack called MaginotDNS that exploits flaws in the bailiwick checking algorithms to take over entire DNS zones, even including top-level domains such as .com. and .net.
“The key to MaginotDNS’s discovery is the inconsistent Bailiwick implementation between different DNS modes,” the researchers explained. “The vulnerabilities do not harm regular forwarders because they do not perform recursive domain resolution, but could have serious consequences for conditional DNS servers (CDNS).”
“CDNS is a popular type of DNS server but has not yet been systematically studied. It is configured to act simultaneously as a recursive resolver and forwarder, and different server modes share the same global cache. As a result, attackers can exploit forwarder vulnerabilities and ‘cross the boundary’ – attacking recursive resolvers on the same server.”