A hitherto undocumented threat actor operating for nearly a decade and codenamed MoustachedBouncer has been attributed to cyber espionage attacks on foreign embassies in Belarus.
“As of 2020, MoustachedBouncer has been able to potentially compromise its targets at the ISP level,” ESET security researcher Matthieu Faou told the group.
Active since at least 2014, it is believed to be linked to anti-Belarusian interests, possibly using legitimate interception systems such as SORM, as well as various devices called nightclubs and discos, to carry out its AitM attacks.
Both Windows malware frameworks support additional spying plugins, including a screen capturer, an audio recorder, and a file stealer. The oldest NightClub sample is dated 19 November 2014, when it was uploaded to VirusTotal from Ukraine.
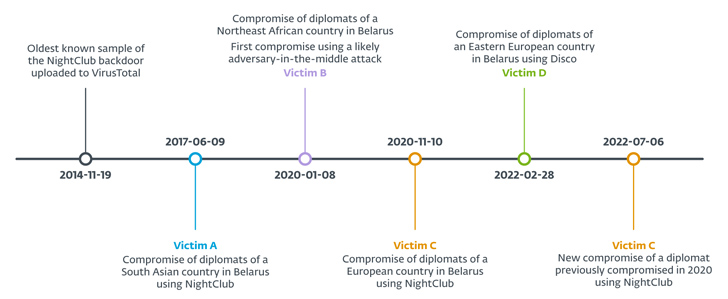
Embassy staff from four different countries have been targeted since June 2017: two from Europe, one from South Asia, and one from Northeast Africa. One of the European diplomats was compromised twice in November 2020 and July 2022. The names of the countries were not revealed.
MoustacheBouncer is believed to be working in conjunction with another advanced persistent threat (APT) actor named Winter Vivern (aka TA473 or UAC-0114), who has a track record of attacking government officials in Europe and the US.
The exact initial infection vector used to distribute the NightClub is currently unknown. On the other hand, distribution of Disco is accomplished through AitM attack.
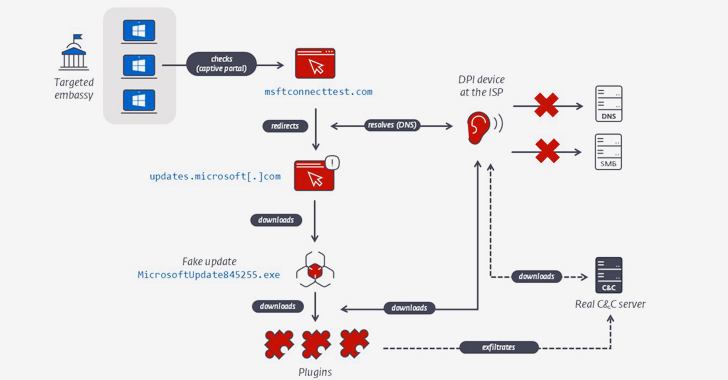
“To compromise their targets, MoustacheBouncer operators tamper with their victims’ Internet access, perhaps at the ISP level, to trick Windows into believing it is behind a captive portal,” Faou said. “For IP ranges targeted by MoustacheBouncer, network traffic is manipulated at the ISP level, and the latter URL redirects to a seemingly valid, but spoofed, Windows Update URL.”
“While collusion of routers to operate AitM on the embassy network cannot be completely ruled out, the presence of legitimate intercept capabilities in Belarus suggests that traffic management is occurring at the ISP level rather than at the target’s routers.” Faou said.
According to the Slovak cyber security company, two Belarusian Internet Service Providers (ISPs), namely Unitary Enterprise A1 and Beltelecom, are suspected of involvement in this campaign.
Victims who land on the bogus are greeted with a message urging them to install critical security updates by clicking on a button. In doing so, a rogue Go-based “Windows Update” installer is downloaded to the machine which, when executed, sets up a scheduled task to run another downloader binary responsible for fetching additional plugins.
Add-ons extend Disco’s functionality by capturing screenshots every 15 seconds, executing PowerShell scripts, and setting up reverse proxies.
An important aspect of the plugins is their use of the Server Message Block (SMB) protocol for data exfiltration to command-and-control servers inaccessible over the Internet, which makes a threat actor’s infrastructure highly resilient.
A January 2020 attack in Belarus targeting diplomats in the northeast African country also used a C# dropper called SharpDisco, which uses two plugins via reverse shell to enumerate connected drives and extract files.
The NightClub framework also includes a Dropper, which, in turn, launches an Orchestrator component to collect files of interest and transmit them over Simple Mail Transfer Protocol (SMTP). Later iterations of NightClub, which appeared in 2017 and 2020, also include a keylogger, audio recorder, screenshotter, and a DNS-tunneling backdoor.
“The DNS-tunneling backdoor (ParametersParser.dll) uses a custom protocol to send and receive data from a malicious DNS server,” Faou explained. “The plugin appends the data to be exfiltrated as part of the subdomain name of the domain used in the DNS request.”
The commands supported by the modular implant allow the threat actor to search for files matching a specific pattern, read, copy and delete files, write files, copy directories, and create arbitrary processes.
NightClub is believed to be used in scenarios where traffic interception is not possible at the ISP level due to anonymity-enhancing mitigations, such as the use of end-to-end encrypted VPNs where Internet traffic is routed outside Belarus .
“The main takeaway is that organizations in foreign countries where the internet cannot be trusted should use an end-to-end encrypted VPN tunnel to a trusted location for all their internet traffic in order to circumvent any network inspection devices,” Faou said.