Threat actors have been observed taking advantage of a now-patched security flaw in Microsoft Windows to deploy an open-source information stealer called Phemedrone Stealer.
“Phemedrone targets data from web browsers and cryptocurrency wallets and messaging apps like Telegram, Steam, and Discord,” said Trend Micro researchers Peter Girnus, Aliakbar Zahravi and Simon Zuckerbraun.
“It also takes screenshots and collects system information regarding hardware, location, and operating system details. The stolen data is then sent to the attackers through Telegram or their command-and-control (C&C) servers. “
The attacks leverage CVE-2023-36025 (CVSS score: 8.8), a security bypass vulnerability in Windows SmartScreen, that could be exploited by tricking a user into clicking on a specially crafted Internet Shortcut (.URL) or a hyperlink pointing to an Internet Shortcut file.
The actively exploited flaw was addressed by Microsoft as part of its November 2023 Patch Tuesday update.
The infection process involves the threat actor hosting malicious Internet shortcut files on cloud services like Discord or FileTransfer.io, as well as obfuscating the links using URL shorteners like Short URLs.
Executing a booby-trapped .URL file allows it to connect to an actor-controlled server and execute a control panel (.CPL) file in a way that prevents Windows Defender SmartScreen by leveraging CVE-2023-36025.
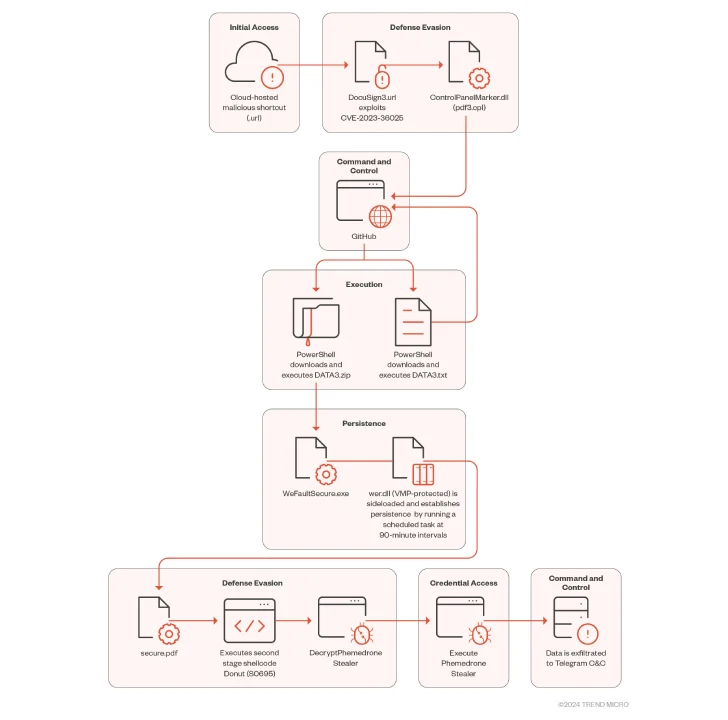
“When the malicious .CPL file is executed through the Windows Control Panel process binary, it calls rundll32.exe to execute the DLL,” the researchers said. “This malicious DLL acts as a loader that calls Windows PowerShell to download and execute the next stage of the attack hosted on GitHub.”
The follow-on payload is a Powershell loader (“DATA3.txt”) that serves as a launchpad for Donut, an open-source shellcode loader that decrypts and executes the Phamedrone stealer.
Written in C#, Phamedrone Stealer is actively maintained by its developers on GitHub and Telegram, facilitating the theft of sensitive information from compromised systems.
This development once again signals that threat actors are becoming increasingly flexible and rapidly adapting their attack chains to take advantage of newly disclosed exploits and cause maximum damage.
“Despite having been patched, threat actors continue to find ways to exploit CVE-2023-36025 and evade Windows Defender SmartScreen protections to infect users with a plethora of malware types, including ransomware and stealers like Phemedrone Stealer,” the researchers said.
