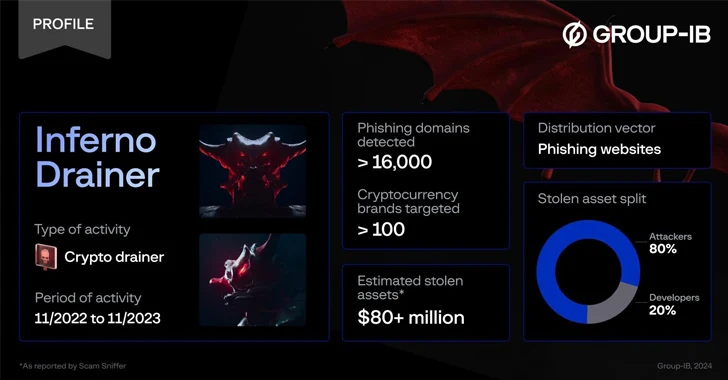
The operators of the now-defunct Inferno Drainer created more than 16,000 unique malicious domains over a one-year period between 2022 and 2023.
The scheme “leveraged high-quality phishing pages to lure unsuspecting users into connecting their cryptocurrency wallets with the attackers’ infrastructure that spoofed Web3 protocols to trick victims into authorizing transactions,” Singapore-headquartered Group-IB said in a report.
Inferno Drainer, which was active from November 2022 to November 2023, is estimated to have made more than $87 million in illicit profits by defrauding more than 137,000 victims.
The malware is part of a broader set of similar offerings available to affiliates under a scam-as-a-service (or drainer-as-a-service) model in exchange for a 20% cut of their earnings.
What’s more, customers of Inferno Drainer could either upload the malware to their own phishing sites, or make use of the developer’s service for creating and hosting phishing websites, either at no extra cost or charging 30% of the stolen assets in some cases.
According to Group-IB, the activity defrauded 100 cryptocurrency brands through specially crafted pages, which were hosted on more than 16,000 unique domains.
Further analysis of 500 of these domains revealed that the JavaScript-based drainer was hosted on a GitHub repository (kuzdaz.github[.]io/seaport/seaport.js) before being directly incorporated into the websites. User “kuzdaz” currently does not exist.
Similarly, another set of 350 sites includes a JavaScript file, “coinbase-wallet-sdk.js”, on a separate GitHub repository, “kasrlorcian.github[.]io”.
These sites were then propagated on sites like Discord and Twitter, enticing potential victims into clicking them under the guise of offering free tokens (aka airdrops) and connecting their wallets, at which point their assets are drained once the transactions are approved.
While using the names seaport.js, coinbase.js and wallet-connect.js, the idea was to mask popular Web3 protocols like seaport, walletconnect and coinbase to complete unauthorized transactions. The earliest website containing one of these scripts is dated May 15, 2023.
“Another distinguishing feature of phishing websites related to Inferno Drainer was that users cannot open the website source code using hotkeys or by right-clicking the mouse,” said Group-IB analyst Viacheslav Shevchenko. “This means that criminals attempted to hide their scripts and illegal activity from their victims.”
It is worth noting that Google-owned Mandiant’s Twitter account was compromised earlier this month to distribute links to a phishing page hosting a cryptocurrency drainer tracked as CLINKSINK.
“Inferno Drainer may have ceased its activity, but its prominence throughout 2023 highlights the severe risks to cryptocurrency holders as drainers continue to develop further,” Andrey Kolmakov, head of Group-IB’s High-Tech Crime Investigation Department, said.
