The nation-state actor linked to North Korea, known as Kimsuky, is suspected of using a previously undocumented Golang-based information stealer called Troll Stealer.
South Korean cybersecurity company S2W said in a new technical report that the malware steals “SSH, FileZilla, C drive files/directories, browsers, system information, [and] screen captures” from infected systems.
Troll Stealer’s connection to Kimsuky stems from its similarity to known malware families, such as the AppleSeed and AlphaSeed malware, which have been attributed to this group.
Kimsuky, also tracked under the names APT43, ARCHIPELAGO, Black Banshee, Emerald Sleet (formerly Thallium), Nickel Kimball, and Velvet Chollima, is known for his propensity to steal sensitive, confidential information in offensive cyber operations.
In late November 2023, the threat actors were sanctioned by the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) for gathering intelligence to further North Korea’s strategic objectives.
In recent months, the adversary group has been held responsible for spear-phishing-attacks targeting South Korean entities providing a variety of backdoors, including AppleSeed and AlphaSeed.
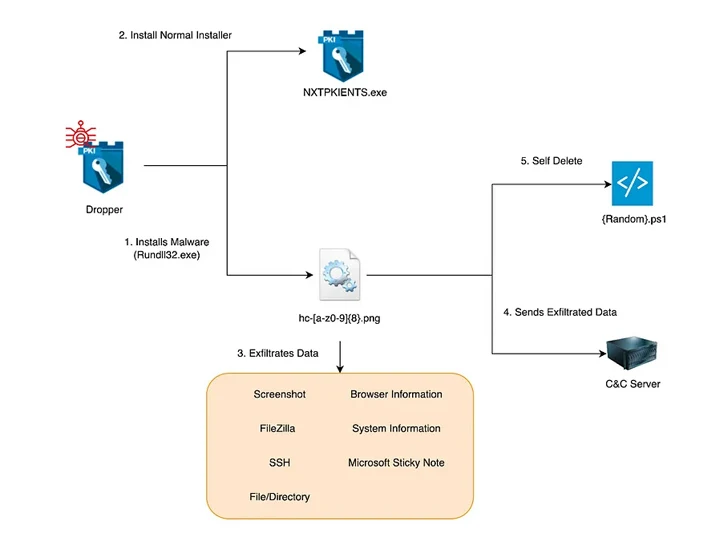
S2W’s latest analysis reveals the use of a dropper that masquerades as a security program installation file from a South Korean company named SGA Solutions to launch the stealer, which gets its name from the path “D:/~/repo/golang/src/root.go/s/troll/agent” that’s embedded in it.
“The dropper runs as a legitimate installer alongside the malware, and both the dropper and malware are signed with a valid, legitimate D2Innovation Co.,LTD’ certificate, suggesting that the company’s certificate was actually stolen,” the company said.
A distinctive feature of Troll Stealer is the ability to steal the GPKI folder on infected systems, increasing the possibility that the malware has been used in attacks targeting administrative and public organizations in the country.
Given the absence of Kimsuky campaigns documenting the theft of GPKI folders, it has raised the possibility that the new behavior is either a shift in tactics or the work of another threat actor closely associated with the group that also has access to the source code of AppleSeed and AlphaSeed.
There are also signs that the threat actor may be involved with a Go-based backdoor codenamed GoBear that’s also signed with a legitimate certificate associated with D2Innovation Co., LTD and executes instructions received from a command-and-control (C2) server.
“Strings in the names of the functions it calls have been found to overlap with commands used by BetaSeed, a C++-based backdoor malware used by the Kimsuky group,” S2W said. “It is notable that GoBear adds SOCKS5 proxy functionality, which was not previously supported by the Kimsuky Group’s backdoor malware.”

9 comments
My brother recommended I might like this web site He was totally right This post actually made my day You cannt imagine just how much time I had spent for this information Thanks
I simply could not go away your web site prior to suggesting that I really enjoyed the standard info a person supply on your guests Is going to be back incessantly to investigate crosscheck new posts
Its like you read my mind You appear to know so much about this like you wrote the book in it or something I think that you can do with a few pics to drive the message home a little bit but instead of that this is excellent blog A fantastic read Ill certainly be back
Thank you for the auspicious writeup It in fact was a amusement account it Look advanced to far added agreeable from you However how can we communicate
I was recommended this website by my cousin I am not sure whether this post is written by him as nobody else know such detailed about my trouble You are amazing Thanks
I loved as much as youll receive carried out right here The sketch is tasteful your authored material stylish nonetheless you command get bought an nervousness over that you wish be delivering the following unwell unquestionably come more formerly again since exactly the same nearly a lot often inside case you shield this hike
I have been browsing online more than three hours today yet I never found any interesting article like yours It is pretty worth enough for me In my view if all website owners and bloggers made good content as you did the internet will be a lot more useful than ever before
Its like you read my mind You appear to know so much about this like you wrote the book in it or something I think that you can do with a few pics to drive the message home a little bit but instead of that this is excellent blog A fantastic read Ill certainly be back
Somebody essentially lend a hand to make significantly articles Id state That is the very first time I frequented your website page and up to now I surprised with the research you made to make this actual submit amazing Wonderful task