Big Head was first documented last month by Fortinet FortiGuard Labs, when it discovered several variants of the ransomware that are designed to encrypt files on victims’ machines in exchange for cryptocurrency payments.
Fortinet researchers said at the time, “A Big Head ransomware variant displayed a fake Windows Update, potentially indicating that the ransomware was also distributed as a fake Windows Update.” “One version has the Microsoft Word icon and was likely distributed as counterfeit software.”
Most of the Big Head specimens presented so far come from the US, Spain, France and Turkey.
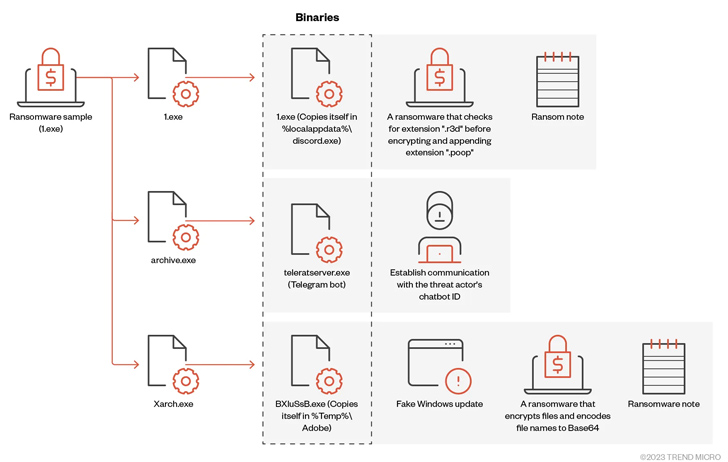
In a new analysis of .NET-based ransomware, Trend Micro details its inner workings, revealing the ability to deploy three encrypted binaries: 1.exe to proliferate the malware, 1.exe to facilitate communications on Telegram, and . Archive for .exe, and Xarch.exe to encrypt, display files and fake windows update.
“When malware displays a fake Windows Update UI to trick the victim into thinking that the malicious activity is a legitimate software update process, the percentage of progress occurs in 100-second increments,” the cyber security company said.
Big Head is no different from other ransomware families in that it deletes backups, terminates multiple processes, and checks to determine that it is running in a virtualized environment before proceeding to encrypt files.
In addition, the malware disables Task Manager to prevent users from checking or terminating its processes and if the machine’s language matches Russian, Belarusian, Ukrainian, Kazakh, Kyrgyz, Armenian, Georgian, Tatar, and Uzbek. If so, it self-destructs. It also includes a self-delete function to erase its presence.
Trend Micro said it detected a second Big Head artifact with ransomware and stealth behavior used to collect web browser history, directory listings, running processes, product keys and network open-source malware May go. The Source takes advantage of the Worldwind stealer.
A third variant of Big Head has also been discovered that includes a file infector called Nesta, which is used to insert malicious code into an executable on an infected host.
“The inclusion of Nesta in ransomware deployments may eventually also serve as a camouflage technique for the Big Head ransomware payload,” said the Trend Micro researchers.
“This technology can make a malware fragment appear as a different type of threat, such as a virus, which can derail the priority of security solutions that primarily focus on ransomware detection.”
The identity of the threatening actor behind Big Head is not yet known, but Trend Micro said it has identified a YouTube channel with the name “Applicasi Premium Quma Quma”, which suggests a likely Indonesian-origin rival.
“Given the diverse functionality of malware, security teams must be prepared,” the researchers concluded. “This multifaceted nature gives malware the ability to cause significant damage once fully operational, making it more challenging to protect systems, as each attack vector requires separate attention.”
