Senior executives working in American-based organizations are being targeted by a new Phishing campaign, which avails a popular adversary-in-the-middle (AiTM) Phishing toolkit, named called EvilProxy to conduct credential harvesting and account takeover attacks.
Menlo Security said that the activity began in July 2023, mainly to create banking and financial services, insurance, property management and real estate and manufacturing sectors.
Security researcher Ravisankar Ramprasad said in a report published last week, “The Threat actors leveraged an open redirection vulnerability on the job search platform ‘indeed.com,’redirecting victims to malicious phishing pages impersonating Microsoft.”
In September 2022, for the first time in the EvilProxy, a reverse proxy, which has been installed between the target and a legitimate login page, is established between the target and a legitimate login page, The credentials were intercepted, the two-factor certification (2FA) code, and for the hijacking of interest for the session cookies.
The threat actors behind the AiTM Phishing Kit are tracked by Microsoft under the moniker Storm-0835 and are estimated to be hundreds of customers.
“These cyber criminals pay a monthly license fee to complete $ 200 to $ 1,000 USD and carry out daily phishing campaigns,” said Tech giant. “Because so many threat actors use these services, it is impractical to mark campaigns for specific actors.”
In the latest set of attacks documented by Menlo Security, victims are sent phishing emails with a deceptive link pointing to Indeed, which, in turn, redirects the individual to an EvilProxy page to harvest the credentials entered.
This is completed by taking advantage of an open redirect flaw, which occurs when the failure to validate the user input causes a vulnerable website that users renew the web pages, to redeem the web pages, to the security railing It sidelines.
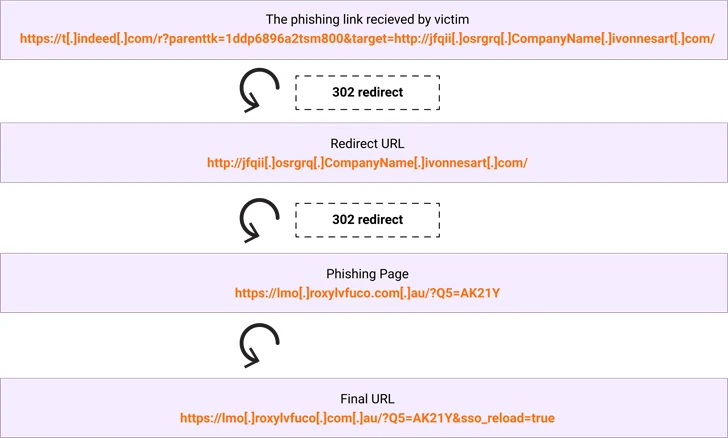
“The subdomain ‘t.indeed.com’ is supplied with parameters to redirect the client to another target (example.com),” Ramprasad said.
“The parameters in the url that follow the ‘?’ Are a combination of parameters unique to indeed.com and the target parameter with argument consists of the destination url. Hence the user upon clicking the URL ends up getting redirected to example.com. In an actual attack, the user would be redirected to a Phishing Page. “
The development Arrives as Threat Actor are Leveragging Dropbox to Create Fake login pages with embedded urls that, when clicked, redirect users to bogus sites that are designed to steal Microsoft account credentials as part of a business email Compromise (BEC) Scheme.
The Check point said, “This is so far another example of how hackers are using legitimate services, which we call BEC 3.0 attack.” “It is incredibly difficult to stop and identify these attacks for both security services and final users.”
Microsoft said in his digital defense report that how “the threat actors are adopting their social engineering techniques and by misusing the cloud-based infrastructure and exploiting reliable business relations technology to fulfill more sophisticated and expensive BEC attacks are using it.
It also comes as the police service of Northern Ireland warned of an uptick in qishing emails, which involve sent an email with a pdf document or a png image file containing a QR CODE in an attempt to sidestep detection and trick Victims into visiting malicious sites and credential harvesting pages.
