Information-stealing malware is actively leveraging an undocumented Google OAuth endpoint called MultiLogin to hijack user sessions and allow continued access to Google services even after password resets.
According to CloudSEK, the key exploit facilitates session persistence and cookie creation, allowing threat actors to maintain access to legitimate sessions in an unauthorized manner.
This technique was first disclosed by a threat actor named PRISMA on his Telegram channel on October 20, 2023. It has since been incorporated into various malware-as-a-service (MaaS) stealth families, such as Lumma, Rhadamanthys, Stealc, Meduza, RisePro, and Whitesnake.
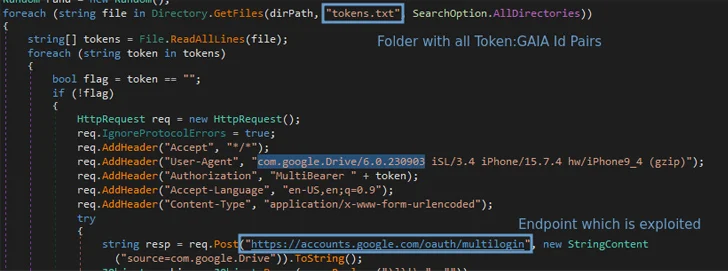
The multilogin authentication endpoint is primarily designed to synchronize Google accounts across services when users sign in to their accounts in the Chrome web browser (i.e., profile).
A reverse engineering of the Lumma stealer code revealed that the technique “targets Chrome’s token_service table of WebData to extract the token and account ID of a logged in Chrome profile,” said security researcher Pavan Karthick M. “This table has two important columns: service(GAIA ID) and encrypted_token.”
This token:GAIA ID pair is combined with the multilogin endpoint to regenerate Google authentication cookies.
Karthick told that three different token-cookie generation scenarios were tested –
- The token can be used any number of times when the user is logged in to the browser.
- When the user changes the password but keeps Google signed in, the token can be used only once because the token has already been used once to keep the user signed in.
- If the user signs out of the browser, the token will be revoked and removed from the browser’s local storage, which will be regenerated upon logging in again.
When contacted for comment, Google acknowledged the existence of the attack method, but noted that users could cancel stolen sessions by logging out of the affected browser.
“Google is aware of recent reports of a malware family stealing session tokens,” the company said. “Attacks involving malware that steal cookies and tokens are not new; we routinely upgrade our defenses against such techniques and to secure users who fall victim to malware. In this instance, Google has taken action to secure any compromised accounts detected.”
“However, it’s important to note a misconception in reports that suggests stolen tokens and cookies cannot be revoked by the user,” it further added. “This is incorrect, as stolen sessions can be invalidated by simply signing out of the affected browser, or remotely revoked via the user’s devices page. We will continue to monitor the situation and provide updates as needed.”
The company has advised users to turn on advanced safe browsing in Chrome to protect themselves from phishing and malware downloads.
“It is advisable to change the password so that threat actors do not use the password reset auth flow to restore the password,” Karthick said. “In addition, users should be advised to monitor their account activity for suspicious sessions that are from IPs and locations they do not recognize.”
“Google’s clarification is an important aspect of user security,” said Alon Gal, co-founder and chief technology officer of Hudson Rock, which first disclosed details of the exploit late last year.
“However, the incident sheds light on a sophisticated exploit that may challenge the traditional methods of securing accounts. While Google’s measures are valuable, this situation highlights the need for more advanced security solutions to counter evolving cyber threats such as in the case of infostealers which are tremendously popular among cybercriminals these days.”
