Multiple security vulnerabilities have been disclosed in the Intelligent Platform Management Interface (IPMI) firmware for Supermicro Baseboard Management Controllers (BMCs), which could result in privilege escalation and execution of malicious code on affected systems.
According to Binarly, the seven vulnerabilities tracked from CVE-2023-40284 to CVE-2023-40290 vary in severity from high to critical, enabling unauthenticated actors to gain root access to BMC systems. Supermicro has sent out a BMC firmware update to fix the bugs.
BMC servers are specialized processors on motherboards that support remote management, which enables administrators to monitor hardware indicators such as temperature, set fan speeds, and update UEFI system firmware. Additionally, BMC chips remain operational even when the host operating system is offline, making them attractive attack vectors for persistent malware deployment.
A brief description of each vulnerability is given below –
- CVE-2023-40284, CVE-2023-40287, and CVE-2023-40288 (CVSS scores: 9.6) – Three cross-site scripting (XSS) flaws that allow remote, unauthenticated attackers to execute arbitrary JavaScript code in the context of the logged-in BMC user.
- CVE-2023-40285 and CVE-2023-40286 (CVSS score: 8.6) – Two cross-site scripting (XSS) flaws that allow remote, unauthenticated attackers to execute arbitrary JavaScript code in the context of the logged-in BMC user by poisoning browser cookies or local storage.
- CVE-2023-40289 (CVSS score: 9.1) – An operating system command injection flaw that allows for the execution of malicious code as a user with administrative privileges.
- CVE-2023-40290 (CVSS score: 8.3) – A cross-site scripting (XSS) flaw that allows remote, unauthenticated attackers to execute arbitrary JavaScript code in the context of the logged-in BMC user, but only when using Internet Explorer 11 browser on Windows
CVE-2023-40289 is “significant because it allows authenticated attackers to gain root access and completely compromise a BMC system,” Binarly said in a technical analysis published this week.
“This privilege allows the attack to continue and infect other endpoints within the compromised infrastructure even when the BMC component is rebooted.”
The other six vulnerabilities – CVE-2023-40284, CVE-2023-40287, and especially CVE-2023-40288 – can be used to create an account with administrator privileges to the web server component of the BMC IPMI software.
As a result, a remote attacker seeking to take control of the server could combine them with CVE-2023-40289 to perform command injection and obtain code execution. In a hypothetical scenario, this could take the form of sending a phishing email to the administrator’s email address which, when clicked, begins the execution of the XSS payload.
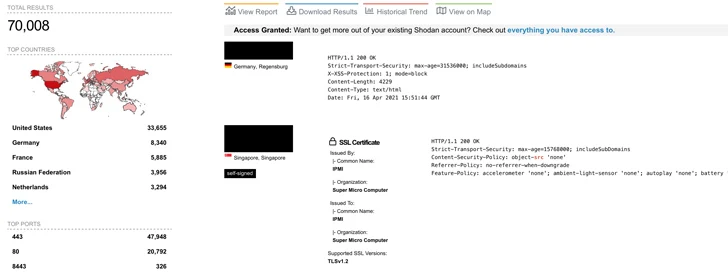
There is currently no evidence of any malicious exploitation of the vulnerabilities in the wild, although Binarly said it has seen more than 70,000 instances of Internet-exposed Supermicro IPMI web interfaces by early October 2023.
“First, it is possible to remotely compromise BMC systems by exploiting vulnerabilities in the web server component exposed to the Internet,” the firmware security company explained.
“An attacker can then gain access to the server’s operating system through legitimate iKVM remote control BMC functionality or by flashing the target system’s UEFI with malicious firmware that allows persistent control of the host OS. From there, any also does not prevent the attacker from lateral movement within the internal network, compromising other hosts.”
Earlier this year, two security vulnerabilities were discovered in the AMI MegaRAC BMC that, if successfully exploited, could allow threat actors to remotely command vulnerable servers and deploy malware.
