Introduction
- The term cyber security is used to refer to the security offered through online services to protect your online information .
- With an increasing amount of people getting connected to Internet, the security threats that cause massive harm are increasing also.
Meaning of the word "cyber"
The word “cyber” is a prefix derived from the word “cybernetics,” which refers to the study of control and communication systems. In the context of technology, “cyber” refers to anything related to the internet or virtual environments.
Need of "cyber security"
The need for cybersecurity arises from the increasing use of internet-connected systems and the growing amount of sensitive information stored and transmitted online. Without proper security measures in place, these systems and data can be vulnerable to cyber attacks such as hacking, malware, and data theft, which can result in financial loss, reputation damage, and loss of privacy. Hence, the need for cybersecurity is essential to protect individuals, organizations, and critical infrastructure from these cyber threats.
Cyber Threat Types
Cyber threats can be classified into the following types:
- Malware: malicious software such as viruses, worms, and Trojans.
- Phishing: attempts to steal sensitive information through deceptive emails or websites.
- Hacking: unauthorized access to systems or networks.
- Ransomware: a type of malware that encrypts a victim’s data and demands payment in exchange for the decryption key.
- Denial of Service (DoS) attacks: attempts to disrupt the availability of a network or website.
- Insider Threats: malicious activities carried out by insiders such as employees, contractors, or vendors.
- Social Engineering: manipulating individuals into divulging confidential information.
- Advanced Persistent Threats (APTs): prolonged and targeted attacks carried out by state-sponsored or organized crime groups.
Types of Cyber Security
There are several types of cybersecurity, including:
- Network security: protection of a computer network from unauthorized access, misuse, and disruptions.
- Endpoint security: protection of individual devices connected to a network, such as laptops and smartphones.
- Application security: protection of software applications from attacks, such as SQL injection and cross-site scripting.
- Cloud security: protection of data and applications in cloud computing environments.
- Data security: protection of sensitive data, such as personal information and financial records, from unauthorized access and breaches.
- Identity and Access Management (IAM): controlling and managing access to systems, networks, and data based on a user’s identity.
- Disaster recovery and business continuity: planning and preparing for data and systems recovery in case of a cyber attack or natural disaster.
- Cryptography: the practice of secure communication, including the encryption of data and authentication of users.
Types of Cyber Attackers
Cyber attackers can be classified into several categories, including:
- Hackers: individuals who carry out unauthorized access to systems or networks.
- Cybercriminals: individuals or groups who use the internet to carry out illegal activities such as theft and fraud.
- Nation-state actors: government-sponsored groups who conduct cyber espionage and cyberattacks.
- Insider Threats: individuals with authorized access to systems or data who carry out malicious activities.
- Activists and hacktivists: individuals or groups who carry out cyberattacks to support a political or social cause.
- Cyber Terrorists: individuals or groups who use the internet to carry out acts of terrorism.
- Script Kiddies: novice hackers who use pre-written scripts to carry out simple cyberattacks.
- Organized Crime Groups: groups who use the internet to carry out large-scale criminal activities such as drug trafficking and human trafficking.
Pillars of Cyber Security
The pillars of cybersecurity are:
- Confidentiality: ensuring that sensitive information is accessible only to authorized parties.
- Integrity: ensuring that data is accurate and unchanged.
- Availability: ensuring that systems and data are accessible to authorized parties when needed.
- Authenticity: verifying the identity of users and devices to prevent unauthorized access.
- Non-Repudiation: ensuring that the sender of a message cannot deny having sent it.
- Privacy: protecting personal and sensitive information from unauthorized access and disclosure.
- Compliance: adhering to legal and regulatory requirements for the handling of sensitive information.
- Resilience: the ability to quickly recover from disruptions and continue normal operations.
Mainly These are:-
- Public
- Processes
- Technology
Cyber Security vs Information Security
Cybersecurity and information security are often used interchangeably, but there is a subtle difference between the two.
Cybersecurity refers to the protection of internet-connected systems, including hardware, software, and data, from cyber attacks and unauthorized access. It involves securing a wide range of technologies, including computers, networks, and mobile devices.
Information security, on the other hand, is a broader term that encompasses cybersecurity as well as the protection of all types of information, including paper documents, and any other medium used to store information. It is a subset of cybersecurity that focuses on securing information regardless of the form it takes or the technology used to store it.
In summary, cybersecurity is a specific aspect of information security that deals with the protection of internet-connected systems and data.
Cybersecurity vs Network Security
Cybersecurity and network security are related but distinct concepts in the field of information security.
Cybersecurity refers to the protection of internet-connected systems, including hardware, software, and data, from cyber attacks and unauthorized access. It encompasses a wide range of technologies and practices aimed at protecting against various types of cyber threats, such as malware, phishing, and hacking.
Network security, on the other hand, is a specific aspect of cybersecurity that deals with the protection of computer networks and the systems connected to them. It involves implementing security measures, such as firewalls, intrusion detection systems, and encryption, to prevent unauthorized access, misuse, and disruption to the network and the systems connected to it.
In summary, network security is a subset of cybersecurity that focuses on the protection of computer networks and the systems connected to them.
Major Security Problems
There are several major security problems that organizations and individuals face today, including:
- Malware: including viruses, trojans, and ransomware that can cause damage to systems and data.
- Phishing: the use of fake emails, websites, and messages to trick people into revealing sensitive information.
- Hacking: unauthorized access to systems and networks to steal sensitive information or disrupt operations.
- Social engineering: the use of psychological manipulation to trick people into revealing sensitive information.
- Insider Threats: employees or contractors who use their authorized access to systems or data to carry out malicious activities.
- Weak passwords: the use of easily guessed or easily cracked passwords to access systems and data.
- Unpatched software: failure to update software with the latest security patches, leaving systems vulnerable to attack.
- Data breaches: unauthorized access to sensitive information, such as personal and financial data, resulting in the theft or exposure of that information.
Viruses and Worms
Viruses and worms are both types of malware that can infect computer systems and cause damage.
A virus is a type of malicious software that attaches itself to a legitimate program or file and spreads to other systems when the infected file is shared or executed. A virus can cause harm to the infected system, such as altering or deleting data, or slowing down performance.
A worm is a type of malware that can self-replicate and spread to other systems without the need for human intervention. Unlike a virus, a worm does not need to attach itself to a legitimate program or file to spread. It can exploit vulnerabilities in operating systems or network services to spread from one system to another.
Both viruses and worms can cause significant harm to computer systems and networks, making it important for individuals and organizations to take measures to protect their systems and data from these types of threats.
Solution
There are several solutions for improving cybersecurity, including:
Antivirus software: software that detects and removes malware from computer systems.
Firewalls: hardware or software that controls incoming and outgoing network traffic based on predefined security rules.
Encryption: the process of encoding information to prevent unauthorized access.
Two-factor authentication: an authentication process that requires users to provide two separate forms of identification, such as a password and a security token.
Network segmentation: dividing a network into smaller, isolated subnets to limit the spread of malware and to improve the overall security of the network.
Intrusion detection and prevention systems: software that monitors network traffic for suspicious activity and takes action to prevent it.
Vulnerability management: the process of identifying and mitigating vulnerabilities in systems and software.
User awareness and training: educating users about cyber threats and how to recognize and avoid them.
Regular software and security updates: installing updates that fix security vulnerabilities and improve the overall security of systems.
Incident response planning: having a plan in place for responding to a cyber attack, including how to contain the attack, recover from it, and prevent future attacks.
Some Anti-viruses
Some popular anti-virus software solutions include:
- Norton AntiVirus
- McAfee AntiVirus
- Kaspersky Anti-Virus
- Bitdefender Anti-Virus
- AVG AntiVirus Free
- Avast Free Antivirus
- ESET NOD32 Antivirus
- Trend Micro Antivirus+ Security
- Windows Defender (built-in to Windows 10)
These anti-virus software solutions offer varying levels of protection and features, so it’s important to research and compare different options to find the best solution for your needs.
Hackers and their types
A hacker is an individual or a group who uses their technical knowledge to gain unauthorized access to computer systems, networks, or data. There are several types of hackers, including:
White Hat Hackers: also known as ethical hackers, these individuals use their hacking skills to identify vulnerabilities in systems and help organizations improve their security.
Black Hat Hackers: also known as malicious hackers, these individuals use their hacking skills to carry out cyber attacks, steal sensitive information, and cause harm to computer systems and networks.
Gray Hat Hackers: these individuals fall between white and black hat hackers, sometimes using their skills for good, but sometimes engaging in malicious activities.
Script Kiddies: individuals who use pre-written scripts or tools to carry out cyber attacks, without having a deep understanding of the underlying technology.
Nation-State Hackers: hackers working on behalf of governments to carry out cyber espionage and other malicious activities.
Regardless of the type of hacker, it’s important for individuals and organizations to take steps to protect their systems and data from unauthorized access.
How to Prevent Hacking
To prevent hacking, you can take the following measures:
Keep software and systems up to date: Regularly update software and systems to fix known vulnerabilities.
Use strong and unique passwords: Use strong passwords and change them regularly, avoiding using the same password for multiple accounts.
Enable two-factor authentication: Add an extra layer of security to your accounts by using two-factor authentication.
Use anti-virus and anti-malware software: Keep your computer protected by using anti-virus and anti-malware software.
Be wary of phishing emails: Don’t click on links or download attachments from unknown or suspicious sources.
Be cautious when using public Wi-Fi: Public Wi-Fi networks can be vulnerable to hacking, so be careful when using them for sensitive transactions.
Use encryption: Use encryption to protect sensitive information when storing it or transmitting it over the internet.
Back up your data: Regularly back up your data to prevent data loss in case of a cyber attack.
Educate yourself and your employees: Stay informed about the latest cyber threats and educate yourself and your employees on how to recognize and avoid them.
Develop an incident response plan: Have a plan in place for responding to a cyber attack, including how to contain the attack, recover from it, and prevent future attacks.
Malware
Malware (short for “malicious software”) refers to any software that is intentionally designed to harm or exploit a computer system, network, or user. Malware can take various forms, including:
Viruses: malicious code that infects other software and replicates itself, causing harm to the infected computer.
Worms: self-replicating malware that spreads from one computer to another over a network.
Trojans: malware that disguises itself as legitimate software and tricks users into installing it, allowing hackers to gain access to the infected computer.
Ransomware: malware that encrypts a user’s files and demands payment in exchange for the decryption key.
Adware: software that displays unwanted advertisements, often bundled with free software downloads.
Spyware: software that collects information about a user’s activity without their knowledge or consent.
It’s important to protect your computer and network from malware by using anti-virus and anti-malware software, keeping software and systems up to date, and being cautious when downloading software or clicking on links from unknown sources.
To Stop Malware
To prevent malware infections, you can take the following measures:
Keep software and systems up to date: Regularly update software and systems to fix known vulnerabilities.
Use anti-virus and anti-malware software: Keep your computer protected by using anti-virus and anti-malware software, and keep the software up to date.
Be wary of phishing emails: Don’t click on links or download attachments from unknown or suspicious sources.
Use strong and unique passwords: Use strong passwords and change them regularly, avoiding using the same password for multiple accounts.
Be cautious when using public Wi-Fi: Public Wi-Fi networks can be vulnerable to malware, so be careful when using them for sensitive transactions.
Keep software up to date: Regularly check for updates for all software on your computer, and install them promptly.
Educate yourself and your employees: Stay informed about the latest malware threats and educate yourself and your employees on how to recognize and avoid them.
Back up your data: Regularly back up your data to prevent data loss in case of a malware attack.
Disable unnecessary software and services: Reduce the attack surface by disabling or uninstalling software and services that are not in use.
Use a pop-up blocker: Use a pop-up blocker to prevent pop-ups and other unwanted advertisements, which can often contain malware.
Trojan Horses
A Trojan horse is a type of malware that disguises itself as legitimate software, often tricking users into downloading and installing it. Once installed, the Trojan can give attackers unauthorized access to the infected computer or steal sensitive information such as passwords, financial data, and personal information. Trojans can also be used to install other types of malware, such as ransomware or spyware, on the infected computer.
To prevent Trojan horse infections, you can take similar measures as you would to prevent malware infections, such as keeping software and systems up to date, using anti-virus and anti-malware software, being wary of phishing emails, and using strong and unique passwords. Additionally, it’s important to only download software from trusted sources and to be cautious when receiving emails or messages that ask you to download an attachment or executable file.
How to Avoid Trojans
To avoid Trojan horse infections, you can take the following measures:
Keep software and systems up to date: Regularly update software and systems to fix known vulnerabilities.
Use anti-virus and anti-malware software: Keep your computer protected by using anti-virus and anti-malware software, and keep the software up to date.
Be wary of phishing emails: Don’t click on links or download attachments from unknown or suspicious sources.
Download software from trusted sources: Only download software from reputable websites and avoid downloading software from torrents or other peer-to-peer networks.
Be cautious when receiving emails or messages that ask you to download an attachment or executable file: If you receive an email or message asking you to download an attachment or executable file, be wary, even if it appears to come from a trusted source.
Use strong and unique passwords: Use strong passwords and change them regularly, avoiding using the same password for multiple accounts.
Be cautious when using public Wi-Fi: Public Wi-Fi networks can be vulnerable to malware, so be careful when using them for sensitive transactions.
Educate yourself and your employees: Stay informed about the latest Trojan horse threats and educate yourself and your employees on how to recognize and avoid them.
Disable unnecessary software and services: Reduce the attack surface by disabling or uninstalling software and services that are not in use.
Regularly back up your data: Regularly back up your data to prevent data loss in case of a Trojan horse attack.
Password Cracking and Securing Password’s
Password cracking is the process of guessing or recovering a password in order to gain unauthorized access to a computer system or online account. Crackers use various techniques to crack passwords, including dictionary attacks, brute force attacks, and social engineering.
To prevent password cracking, you can take the following measures:
Use strong passwords: Use a combination of letters, numbers, and symbols to create a strong password that is difficult to crack.
Avoid using the same password for multiple accounts: Using the same password for multiple accounts increases the risk of a password being cracked and multiple accounts being compromised.
Enable two-factor authentication (2FA): 2FA adds an extra layer of security to your accounts by requiring a secondary form of authentication, such as a code sent to your phone, in addition to your password.
Regularly change passwords: Regularly changing your passwords can help prevent crackers from accessing your accounts, even if they have obtained your password through a previous breach.
Educate yourself and your employees: Stay informed about the latest password cracking techniques and educate yourself and your employees on how to create and manage secure passwords.
Use a password manager: A password manager can help you generate strong passwords, store them securely, and automatically enter them into websites and applications.
Cyber Security is Everyone’s Responsibility

Cyber Security Strategy-India
- Security Policy, Legal Framework
- –IT Act, 2000
- –IT(Amendment) Bill, 2006 – Data Protection & Computer crimes
- Capacity building
- –Skill & Competence development
- Research and Development
- –Cyber Monitoring
- –Network Security
- International Collaboration
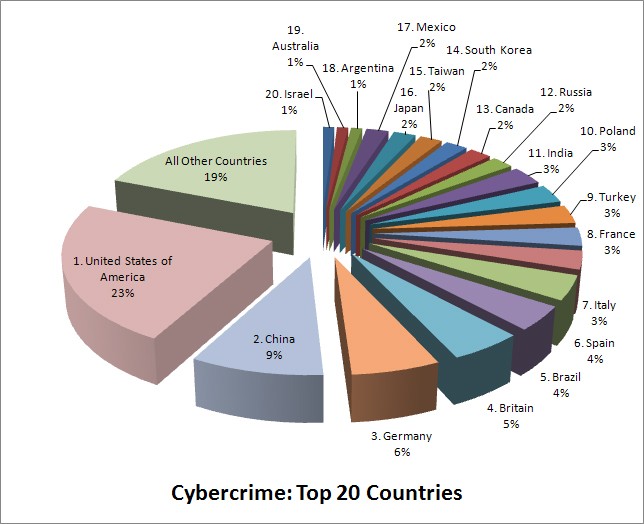
World Cyber Crime Chart
India Stands 11th in the Cyber Crime in the World
Conclusion
I hope that my presentation will be helpful for my lovely & sweet audience to improve their knowledge about cyber security and to overcome several security loopholes on their computer operation. Also it helps to spread awareness among normal people about emerging security threats. Simple and practical prevention methods are explained in the seminar to prevent PCs from infection.

1 comment
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.