Exposed Kubernetes (K8s) clusters are being exploited by malicious actors to deploy cryptocurrency miners and other backdoors.
In a report, cloud security firm Aqua said most of the clusters belonged to small to medium-sized organizations, with a smaller subgroup belonging to large companies spanning the financial, aerospace, automotive, industrial and security sectors.
In total, Kubernetes clusters belonging to more than 350 organizations, open-source projects and individuals were discovered, 60% of which were the target of an active crypto-mining campaign.
Publicly accessible clusters, according to Aqua, suffer from two different types of misconfiguration: allowing anonymous access with elevated privileges and the “–address=`0.0.0.0` –accept-hosts`*`” flags running kubectl proxy with .
“Housing a wide array of sensitive and valuable assets, Kubernetes clusters can store customer data, financial records, intellectual property, access credentials, secrets, configurations, container images, infrastructure credentials, encryption keys, certificates, and network or service information,” security researchers Michael Katchinskiy and Assaf Morag said.
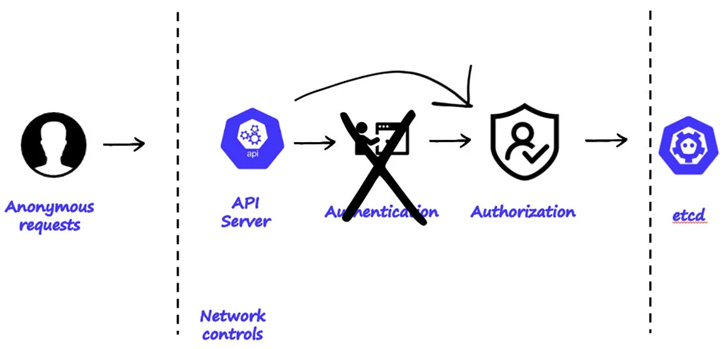
Pod lists containing sensitive environment variables and access keys are found in exposed K8s clusters, which can be used by bad actors to gain deeper access to target environments, access source code repositories, and worse, if possible, introduce malicious modifications can be done.
A closer examination of the groups revealed three separate operations aimed at cryptocurrency mining, including the Dero cryptojacking operation, RBAC Buster, and TeamTNT’s SilentBob.
“Despite the serious security implications, such misconceptions are prevalent in organizations regardless of size, indicating a gap in the understanding and management of Kubernetes security,” the researchers said.
