The threat actors behind the HiatusRAT malware have returned from their hiatus with a new wave of reconnaissance and targeting activity aimed at Taiwan-based organizations and the US military procurement system.
In addition to recompiling malware samples for different architectures, the artifacts have been hosted on new Virtual Private Servers (VPS), Lumen Black Lotus Labs said in a report published last week.
The cyber security firm described the activity cluster as “brazen” and “one of the most daring” that shows no sign of slowing down. The identity and origin of those making the threats are currently unknown.
The targets included commercial firms such as semiconductor and chemical manufacturers, and at least one municipal government organization in Taiwan, as well as US Department of Defense (DOD) servers associated with submitting and retrieving proposals for defense contracts.
HiatusRAT was first revealed in March 2023 by the cyber security company as part of a campaign launched in July 2022 targeting business-grade routers to covertly spy on victims based primarily in Latin America and Europe.
At least 100 edge networking devices globally were infected to passively collect traffic and turn them into proxy networks of command-and-control (C2) infrastructure.
The latest set of attacks, observed from mid-June to August 2023, involve the use of pre-built HiatusRAT binaries specifically designed for the Arm, Intel 80386 and x86-64 architectures, along with MIPS, MIPS64 and i386.
A telemetry analysis to determine connections made to servers hosting the malware showed that “over 91% of inbound connections came from Taiwan, and it appears that Ruckus-manufactured edge devices were preferred.”
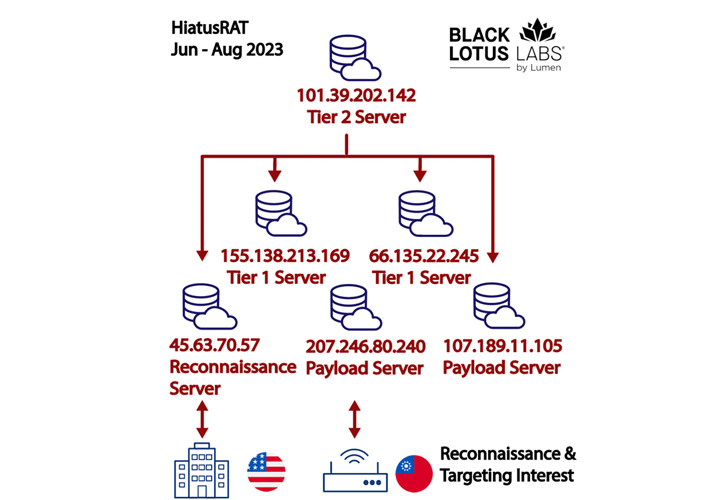
The HiatusRAT infrastructure consists of payload and reconnaissance servers, which communicate directly with the victim’s network. These servers are commanded by Tier 1 servers which, in turn, are operated and managed by Tier 2 servers.
The attackers have been identified as using two different IP addresses 207.246.80[.]240 and 45.63.70[.]57 to connect to DoD servers for a period of approximately two hours on June 13 . 11 MB of bi-directional data is estimated to be transferred during this period.
It is not clear what the ultimate goal is, but it is suspected that the adversary may have been looking for publicly available information related to current and future military contracts for future targets.
Targeting perimeter assets such as routers has become a pattern in recent months, with China-linked threat actors exploiting security flaws in unpatched Fortinet and SonicWall devices to establish long-term persistence within target environments.
“Despite prior disclosure of equipment and capabilities, the threat actor took the smallest of steps to replace existing payload servers and continued its operations, without attempting to reconfigure its C2 infrastructure,” the company said.
