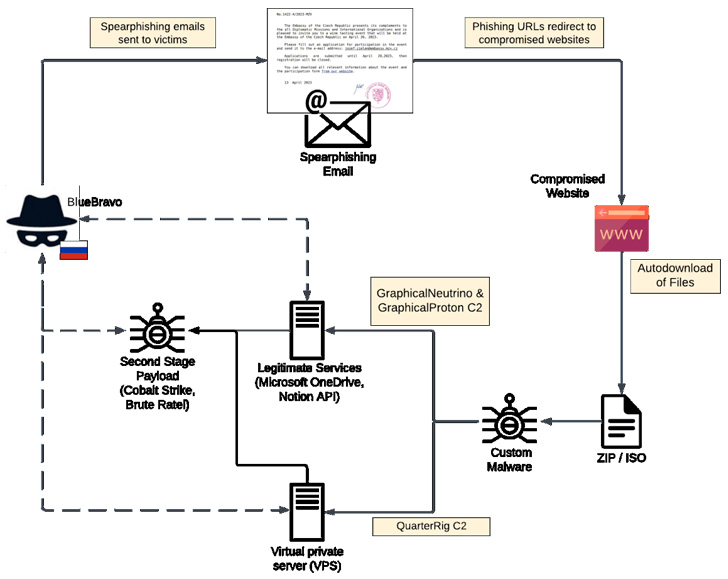
Phishing campaigns are characterized by the use of legitimate Internet services (LIS) for command-and-control (C2) obscurity, Recorded Future said in a new report published on Thursday. This activity was observed between March and May 2023.
Bluebravo, also known as APT29, Cloaked Ursa, and Midnight Blizzard (formerly Nobelium), is attributed to Russia’s Foreign Intelligence Service (SVR), and has in the past attacked Dropbox, Firebase, Google Drive, Notion And have used Trello. Locates infected hosts and communicates covertly with them.
To that end, GraphicalProton is the latest addition to a long list of malware targeting diplomatic organizations, following Graphical Neutrino (aka Snowyember), Hafrig, and Quarterrigg.
“Unlike GraphQL Neutrino, which uses Notion for C2, GraphQLProton uses Microsoft’s OneDrive or Dropbox for communication,” the cybersecurity firm said.
This is an attempt on the part of Bluebravo operators not only to diversify their tooling but also to expand the portfolio of services to be misused to target organizations of strategic interest to the nation.
“BlueBravo appears to prioritize cyber espionage efforts against entities in the European public sector, possibly due to the Russian government’s interest in strategic data during and after the war in Ukraine.”
The new malware strain, like GraphicalNeutrino, acts as a loader and is staged within an ISO or ZIP file distributed via vehicle-themed lure phishing emails, the Palo Alto Networks unit reported earlier this month. There is overlap with the intrusion set reported by 42.
The ISO files contained .LNK files allegedly disguised as .PNG images of a BMW car for sale, which when clicked deployed GraphicalProton for a follow-on exploit. This is achieved by using Microsoft OneDrive as C2 and periodically polling a folder in the storage service to fetch additional payloads.
“It is important for network defenders to be aware of the potential for abuse of these services within their enterprise and to recognize instances in which they may be used in similar attempts to exfiltrate information,” the researchers said.
The development comes as Ukraine’s Computer Emergency Response Team (CERT-UA) warned of ongoing phishing attacks being carried out by a group known as the UAC-0006 group, which the agency said is a smokeloader. There is a back door. Efforts are being intensified to entice users to install
