Threat actors belonging to the hacking team known as Patchwork have been seen targeting universities and research organizations in China as part of a recent campaign.
According to the KnownSec 404 team, this activity involved the use of a backdoor codenamed EyeShell.
Patchwork, also known as Operation Hangover and Zinc Emerson, is a terrorist group suspected to be operating from India. Active since at least December 2015, the attack series launched by the organization have a narrow focus and have been used to isolate Pakistan and China through spear-phishing and watering hole attacks with custom implants such as BADNEWS Has gone.
The rival group has been found to share strategic overlap with other cyber-espionage groups with Indian connections, including Sidewinder and the DoNot Team.
Earlier this May, Meta revealed it removed 50 accounts on Facebook and Instagram powered by Patchwork that uploaded videos to the Google Play Store to collect data from victims in Pakistan, India, Bangladesh, Sri Lanka, Tibet & China And took advantage of rogue messaging apps.
“Patchwork relies on a series of elaborate fictional personas to socially engineer people to click on malicious links and download malicious apps,” the social media giant said.
“These apps included relatively basic malicious functionality with access to user data, which was entirely dependent on valid app permissions granted by the end user. Specifically, Patchwork created a fake review website for chat apps, where They listed the top five communications apps, with their own, attacker-controlled app at the top of the list.”
Some of its activities have also been reported under the name ModifiedElephant, according to Secureworks, referring to a set of attacks against human rights activists, academics, and lawyers across India to conduct long-term surveillance and plant “incriminating digital evidence” in connection with the 2018 Bhima Koregaon violence in the state of Maharashtra.
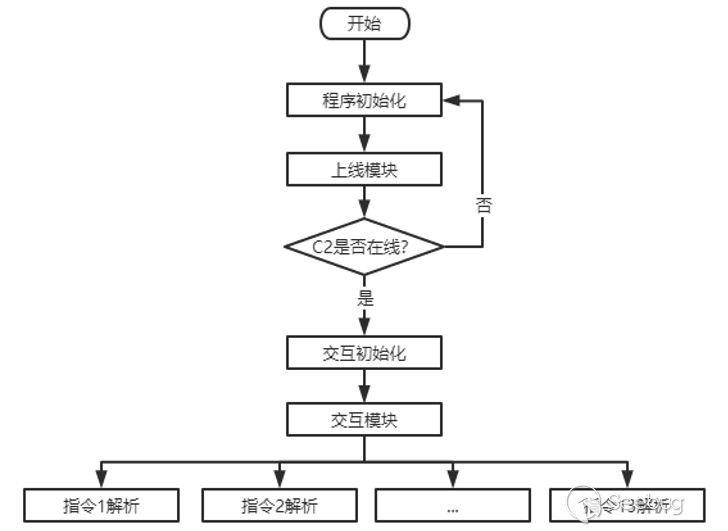
EyeShell, detected alongside BADNEWS, is a a .NET-based modular backdoor that comes with capabilities to establish contact with a remote command-and-control (C2) server and execute commands to enumerate files and directories, downloading and uploading files to and from the host, execute a specified file, delete files, and capture screenshots.
The findings came as the cyber security company also detailed another wave of phishing attacks carried out by a group called Bitter with a new backdoor called ORPCBackdoor on aerospace, military, large enterprises, national government affairs and universities in the country.
The South Asian threat actor was previously detected targeting the nuclear power industry in China with malware downloaders distributed via CHM and Microsoft Excel files, which are designed to create persistence and retrieve further payloads.
