Organizations in Italy are the target of a new phishing campaign that takes advantage of a new type of malware called Wikiloader with the ultimate aim of installing a banking trojan, stealer and spyware called Ursnif (aka Gozi).
“This is a sophisticated downloader with the aim of installing a second malware payload,” Proofpoint said in a technical report. “The malware uses a number of mechanisms to avoid detection and was likely developed as a form of malware that can be hired to selectively target cybercriminal threat actors.”
Wikiloader is so named because of malware requesting Wikipedia and checking that the response contains the string “The Free”.
The enterprise security firm said it first detected the malware in the wild on December 27, 2022, in connection with an intrusion set planted by a threat actor named TA544, also known as Bamboo Spider and Zeus Panda.
The campaigns focused on the use of emails containing Microsoft Excel, Microsoft OneNote, or PDF attachments that served as a lure to deploy the downloader, which is then used to install Ursnif.
In an indication that Wikiloader is shared among several cybercrime groups, in late March 2023 a threat actor named TA551 (aka Shathak) has also been observed using the malware.
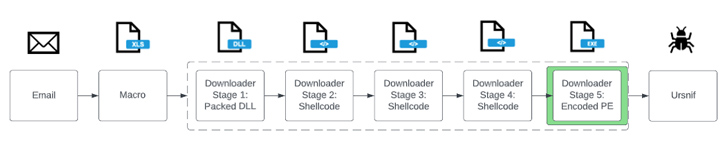
Recent TA544 campaigns detected in mid-July 2023 have utilized accounting themes to propagate PDF attachments with URLs that, when clicked, lead to the delivery of a ZIP archive file, which, in turn, packs a JavaScript file designed to download and execute WikiLoader.
Wikiloader is highly obscure and comes with deceptive tricks to bypass endpoint protection software and avoid exploding into automated analysis environments. It has also been engineered to retrieve and run shellcode payloads hosted on Discord, which are eventually used to launch Ursnif.
“It is currently under active development, and its authors are making regular changes to try to remain anonymous and fly under the radar,” Proofpoint senior threat intelligence analyst Selena Larsen said in a statement.
“It is likely that more criminal threat actors will use this, particularly those known as Early Access Brokers (IABs) who conduct routine activity that leads to ransomware. Defenders need to be aware of this new malware and the activities involved in payload delivery and take steps to protect their organizations from exploitation.”
