Vulnerable Redis services have been targeted by a “new, improved, dangerous” variant of the malware called Skidmap that has been engineered to target a wide range of Linux distributions.
“The malicious nature of this malware is to adapt to the system on which it is executed,” Trustwave security researcher Radoslav Zdonzik said in an analysis published last week.
The Linux distributions Skidmap is eyeing include Alibaba, Anolis, OpenEuler, EulerOS, Streams, CentOS, RedHat, and Rocky.
Skidmap was first disclosed by Trend Micro in September 2019 as a cryptocurrency mining botnet with the ability to load malicious kernel modules that could obscure its activities as well as monitor the miner process.
The operators of the malware were also found hiding their backup command-and-control (C2) IP addresses on the bitcoin blockchain, indicating another botnet malware called Glupteba.
Akamai said in February 2021, “The technology to fetch real-time data from a decentralized and essentially uncensored data source to generate C2 IP addresses makes transitions difficult to overcome and C2 IP addresses simple and fast.”
The latest attack chain documented by Trustwave involves breaching poorly secured Redis server instances to deploy a dropper shell script designed to distribute an ELF binary that masquerades as a GIF image file.
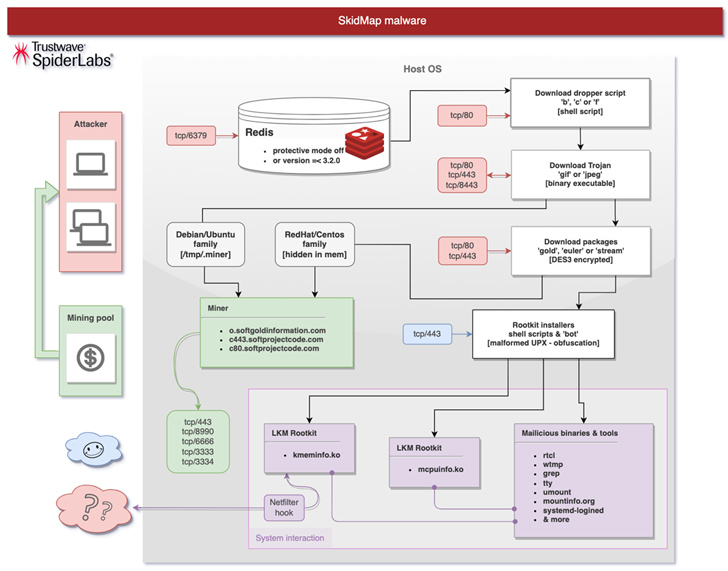
The binary then proceeds to add the SSH key to the “/root/.ssh/authorized_keys” file, disable SELinux, set up a reverse shell that pings an actor-controlled server every 60 minutes, and Finally downloads an appropriate package (named gold, stream, or euler) based on the Linux distribution and kernel used.
The package, on its part, comes with several shell scripts to install kernel modules and take steps to cover tracks by purging logs, and launches a botnet component capable of recovering additional rootkit payloads: mcpuinfo.ko, to hide the miner process, and kmeminfo.ko, to analyze, modify, or drop network packets.
The miner binary itself is also downloaded, although in some variants, “the underlying miner from the extracted ‘gif’ binary file” is used.
“The level of advancement of this malware is really high, and detection, especially in large server infrastructures, can be very difficult,” Zdonczyk said. “When testing this on home computers, the only serious indicator that something was wrong was excessive operation of the fans, and in the case of laptops, case temperature.”
