New research has revealed that threat actors are abusing Cloudflare tunnels to establish covert communication channels from compromised hosts and maintain persistent access.
“Cloudflare is functionally very similar to ngrok,” said Nic Finn, senior threat intelligence analyst at GuidePoint Security. “However, Cloudflare differs from ngrok in that it provides a lot of usability for free, including the ability to host TCP connectivity on Cloudflare.”
A command-line tool for Cloudflare tunnels, Cloudflare allows users to create secure connections between the origin web server and Cloudflare’s closest data center to hide the web server IP address as well as prevent volumetric distributed denial-of-service (DDoS) and Brute-force login attacks can be blocked.
For a threat actor with advanced access to an infected host, this feature presents an attractive approach to gain a foothold by generating the tokens required to establish a tunnel from the victim machine.
“The tunnel updates as soon as the configuration change is made in the Cloudflare Dashboard, allowing TAs to enable functionality only when they want to conduct activities on the victim machine, then disable functionality to prevent exposure of their infrastructure,” Finn explained.
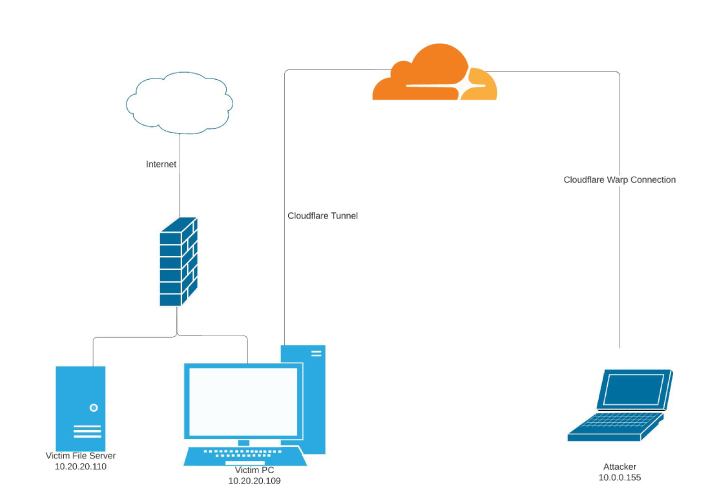
“For example, a TA may enable RDP connectivity, collect information from the victim machine, then disable RDP until the next day, thus preventing detection of the domain used to establish the connection or The ability to observe decreases.”
Even more troubling, the adversary could take advantage of the tunnel’s Private Networks functionality to stealthily access a range of IP addresses (i.e., endpoints within a local network) as if they were “physically collocated with the victim machine hosting the tunnel.”
That said, this technology has already found buyers in the wild. Earlier this year, Phylum and Kroll detailed two separate software supply chain attacks targeting the Python Package Index (PyPI) repository, using Cloudflare to remotely access the endpoint via a Flask web application fraudulent packages were detected while downloading.
Finn said, “Organizations legitimately using Cloudflare services could potentially limit their services to specific data centers and Cloudflare tunnels like trace traffic that goes anywhere except their designated data centers ” “This method can aid in the detection of unauthorized tunnels.”
To identify potential abuse of Cloudflare, it is recommended that organizations implement adequate logging mechanisms to block attempts to download executables, as well as monitor incompatible commands, DNS queries, and outbound connections.
