Microsoft is warning of a new phishing campaign run by an early access broker that involves using Teams messages as bait to infiltrate corporate networks.
The tech giant’s Threat Intelligence team is monitoring the cluster named Storm-0324, which is also known by the monikers TA543 and Sagrid.
“As early as July 2023, Storm-0324 was observed distributing payloads using an open-source tool to send phishing lures via Microsoft Teams chat,” the company said, adding the development marks a shift from using email-based initial infection vectors for initial access.
Storm-0324 operates as a payload distributor in the cybercriminal economy, providing a service that allows the dissemination of various payloads using evasive infection chains. This includes a mix of downloaders, banking trojans, ransomware, and modular toolkits such as Nymaim, Gozi, Trickbot, IcedID, Gootkit, Dridex, Sage, GandCrab, and JSSLoader.
Attack sequences run by the actor in the past have employed invoice- and payment-themed decoy email messages to trick users into downloading SharePoint-hosted ZIP archive files, which distribute JSSLoader, a malware loader. Which is capable of profiling infected machines and loading additional payloads.
“The actor’s email chains are highly fraudulent, in that they use traffic delivery systems (TDS), such as BlackTDS and Keitaro, which provide the ability to identify and filter user traffic,” Microsoft said.
“This filtering capability allows attackers to avoid detection by certain IP ranges that may include security solutions such as malware sandboxes, while also successfully redirecting victims to their malicious download site.”
The access afforded by the malware paves the way for the ransomware-as-a-service (RaaS) actor Sangria Tempest (aka Carbon Spider, ELBRUS, and FIN7) to conduct post-exploitation actions and deploy file-encrypting malware.
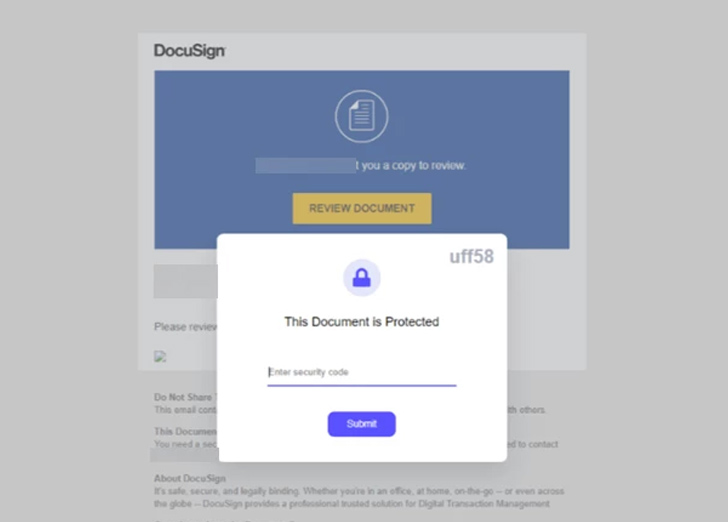
There is a new change in functionality from July 2023, in which a phishing lure is sent to Teams with a malicious link, creating a malicious zip file hosted on SharePoint.
This is accomplished by leveraging an open-source tool called TeamsPisher, which enables Teams tenant users to attach files to messages sent to external tenants by exploiting an issue first exposed by JUMPSEC in June 2023.
It is worth noting that similar techniques were used by Russian nation-state actor APT29 (aka Midnight Blizzard) in attacks targeting approximately 40 organizations globally in May 2023.
The company said it has made several security improvements to stop the threat and that it has “suspended identified accounts and tenants associated with inauthentic or fraudulent behavior.”
Microsoft further explained, “Because Storm-0324 blocks access to other threat actors, identifying and remediating Storm-0324 activity can prevent more dangerous follow-on attacks such as ransomware.”
The revelation comes as Kaspersky detailed the tactics, techniques and procedures of the notorious ransomware group known as Cuba (aka Colddraw and Tropical Scorpius), as well as identifying a new alias called V Is Vendetta , which is suspected to have been used by a sub-group or affiliate.
The group, like RaaS schemes, uses a dual extortion business model to attack multiple companies around the world and generate illicit profits.
Ingress routes entail the exploitation of ProxyLogon, ProxyShell, ZeroLogon, and security flaws in Veeam Backup & Replication software to deploy a custom backdoor dubbed BUGHATCH, which is then used to deliver Cobalt Strike and updated versions of BURNTCIGAR in order to terminate security software running on the host.
“The Cuba cybercrime gang uses an extensive arsenal of both publicly available and custom-made tools, which it keeps up to date, and uses a variety of techniques and methods, including quite dangerous methods such as BYOVD,” Kaspersky said. “
2023 sees major increase in ransomware attacks, U.K. The National Cyber Security Center (NCSC) and the National Crime Agency (NCA) have noted that they are “reliant on a complex supply chain.”
“Focusing on specific ransomware strains could be confusing at best and counterproductive at worst,” the agencies said in a report published earlier this week. “Most ransomware incidents are not caused by sophisticated attack techniques; initial access to victims is gained opportunistically, with success usually the result of poor cyber hygiene.”
