The open-source remote access Trojan known as Quasar RAT has been observed taking advantage of DLL side-loading to fly under the radar and silently siphon data from compromised Windows hosts.
“This technique takes advantage of the inherent trust of these files within the Windows environment,” Uptycs researchers Tejaswini Sandapolla and Karthikkumar Kathiresan said in a report published last week. Detailing the malware’s reliance on ctfmon.exe and calc.exe as part of its attack chain.
Also known as CinaRAT or Yggdrasil, Quasar RAT is a C#-based remote administration tool capable of obtaining system information, a list of running applications, files, keystrokes, screenshots, and executing arbitrary shell commands.
DLL side-loading is a popular technique adopted by many threat actors to execute their own payload by planting a fake DLL file with a name that is recognizable to an individual looking for a benign executable.
“Adversaries use side-loading as a means to conceal actions taken under a potentially legitimate, trusted, and potentially advanced system or software process,” MITRE writes in its explanation of the attack methodology.
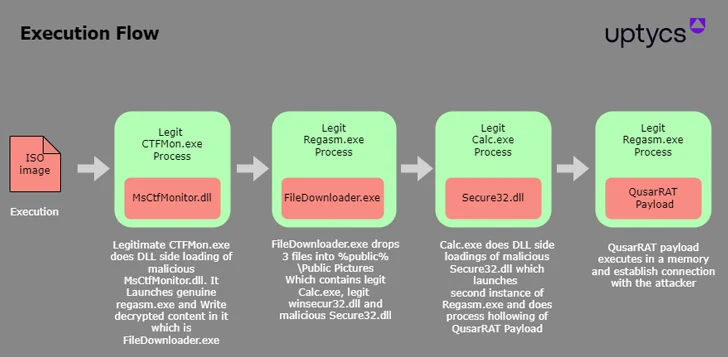
The starting point of the attack documented by Uptycs is an ISO image file containing three files: a legitimate binary named ctfmon.exe named eBill-997358806.exe, a MsCtfMonitor.dll file named monitor.ini, And a malicious MsCtfMonitor.dll.
The researchers said, “When the binary file ‘eBill-997358806.exe’ is run, it initiates the loading of a file named ‘MsCtfMonitor.dll’ (name hidden) through DLL side-loading technology, within which The malicious code is hidden.”
The hidden code is another executable “FileDownloader.exe” that’s injected into Regasm.exe, the Windows Assembly Registration Tool, in order to launch the next stage, an authentic calc.exe file that loads the rogue Secure32.dll again through DLL side- loading and launching the final Quasar RAT payload.
The trojan, for its part, establishes connections with a remote server to send system information and even sets up a reverse proxy for remote access to the endpoint.
The identity of the threat actor and the exact initial access vector used to pull off the attack is unclear, but it’s likely to be disseminated by means of phishing emails, making it imperative that users be on the guard for dubious emails, links, or attachments.
