Poorly secured Microsoft SQL (MS SQL) servers are being targeted in the U.S., European Union, and Latin American (LATAM) regions as part of an ongoing economically motivated campaign to gain early access .
“The analyzed threat campaign appears to end in one of two ways, either the selling of ‘access’ to the compromised host, or the ultimate delivery of ransomware payloads,” Securonix researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov said in a technical report.
The campaign involving actors of Turkish origin has been named RE#TURGENCE by the cyber security firm.
Initial access to the server involves conducting brute-force attacks, followed by using the xp_cmdshell configuration option to run shell commands on the compromised host. This activity mirrors an earlier campaign called DB#JAMMER that surfaced in September 2023.
This step paves the way for the retrieval of the Powershell script from a remote server that is responsible for fetching an obfuscated Cobalt Strike Beacon payload.
The post-exploitation toolkit is used to download the AnyDesk Remote Desktop application from a mounted network share to access the machine and download additional tools like Mimikatz to gather credentials and Advanced Port Scanner to perform reconnaissance.
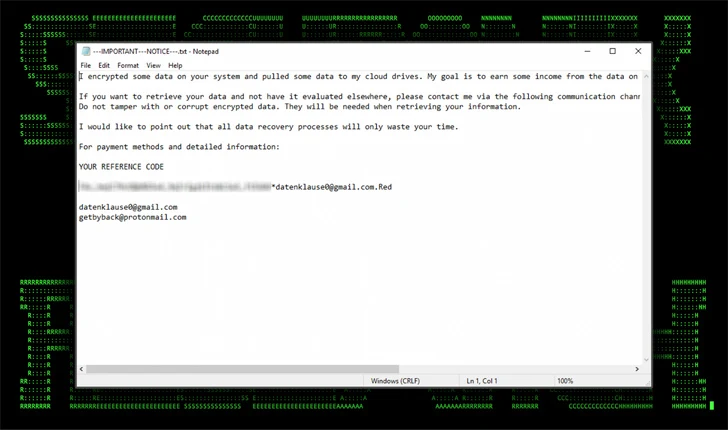
Lateral movement is accomplished through a legitimate system administration utility called PsExec, which can execute programs on remote Windows hosts.
That attack chain ultimately ends with the deployment of mimic ransomware, a variant of which was also used in the DB#JAMMER campaign.
Securonix said it uncovered an operational security (OPSEC) mistake made by threat actors that allowed it to monitor clipboard activity due to the fact that AnyDesk’s clipboard sharing feature was enabled.
This made it possible to know his Turkish origins and his online alias atseverse, which also matches a profile on Steam and a Turkish hacking forum called SpyHack.
“Always avoid exposing critical servers directly to the Internet,” the researchers warned. “In the case of RE#TURGENCE the attackers were able to brute-force their way into the servers directly from outside the main network.”
