Indian government entities and the defense sector have been targeted by a phishing campaign designed to drop Rust-based malware to collect intelligence.
The activity, which was first discovered in October 2023, has been named Operation RusticWeb by enterprise security firm SEQRITE.
Security researcher Sathvik Ram Prakki said, “New Rust-based payloads and encrypted PowerShell commands have been used to infiltrate confidential documents into a web-based service engine instead of a dedicated command-and-control (C2) server. “
Tactical overlap has been highlighted between the cluster and those widely tracked under the Transparent Tribe and Sidecopy aliases, both believed to be linked to Pakistan.
Sidecopy is also a questionable subordinate element within the transparent tribe. Last month, SEQRITE detailed several campaigns carried out by a threat actor targeting Indian government bodies to distribute several trojans such as AllaKore RAT, Ares RAT, and DRat.
Other recent attack chains documented by ThreatMon have employed decoy Microsoft PowerPoint files as well as specially crafted RAR archives susceptible to CVE-2023-38831 for malware delivery, enabling unbridled remote access and control.
“Sidecopy APT Group’s infection chain consisted of multiple steps, each of which was carefully orchestrated to ensure a successful compromise,” ThreatMon said earlier this year.
The latest set of attacks commences with a phishing email, leveraging social engineering techniques to trick victims into interacting with malicious PDF files that drop Rust-based payloads for enumerating the file system in the background while displaying the decoy file to the victim.
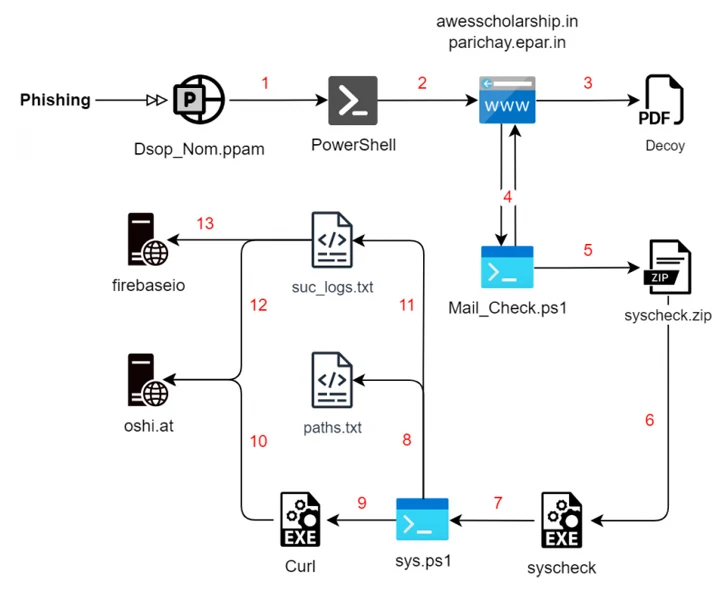
In addition to collecting files of interest, the malware is equipped to collect system information and transmit them to C2 servers, but it lacks the features of other advanced stealth malware available in the cyber crime underground.
A second infection chain identified by SEQRITE in December employs a similar multi-stage process, but replaces the Rust malware with a PowerShell script that takes care of the enumeration and exfiltration steps.
But in an interesting twist, the final-stage payload is launched via a Rust executable that goes by the name “Cisco AnyConnect Web Helper.” The gathered information is ultimately uploaded to oshi[.]at domain, an anonymous public file-sharing engine called OshiUpload.
Ram Prakki said, “Operation Rusticweb could be linked to the APT threat as it has similarities with various Pakistan-linked groups.”
The disclosure comes nearly two months after Cyble revealed a malicious Android app used by the DoNot team targeting individuals in India’s Kashmir region.
The nation-state actor, also known by the names APT-C-35, Origami Elephant, and SECTOR02, is believed to be of Indian origin and has a history of utilizing Android malware to infiltrate devices belonging to people in Kashmir and Pakistan.
The variant examined by Cyble is a trojanized version of an open-source GitHub project called “QuranApp: Read and Explore” that comes fitted with a wide range of spyware features to record audio and VoIP calls, capture screenshots, gather data from various apps, download additional APK files, and track the victim’s location.
Cyble said, “The DoNot group’s continued efforts to refine their tools and techniques underscore the threat they pose, particularly in targeting individuals in India’s sensitive Kashmir region.”

2 comments
I have been struggling with this issue for a while and your post has provided me with much-needed guidance and clarity Thank you so much
You have a way of making each of your readers feel seen and heard That’s a special quality that not all bloggers possess Thank you for creating a safe space for us