The AvosLocker ransomware gang has been linked to attacks against critical infrastructure sectors in the US, some of which were detected as recently as May 2023.
That’s according to a new joint cybersecurity advisory released by the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) detailing the ransomware-as-a-service (RaaS) operation’s tactics, techniques, and procedures (TTPs).
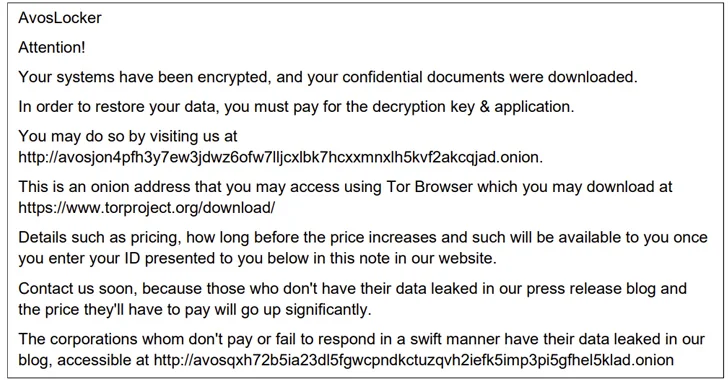
“AvosLocker associates compromise organizations’ networks using legitimate software and open-source remote system administration tools,” the agencies said. “AvosLocker affiliates use intrusion-based data extortion tactics with threats to leak and/or publish stolen data.”
The ransomware strain first emerged in mid-2021, and has since taken advantage of sophisticated techniques to disable antivirus protection as a measure to avoid detection. This affects Windows, Linux, and VMware ESXi environments.
A key hallmark of AvoSlocker attacks is their reliance on open-source tools and living-off-the-land (LotL) tactics, which leave no trace behind. Tunneling tools like Chisel and Ligolo, along with legitimate utilities like FileZilla and Rclone, are used for data exfiltration.
Command-and-control (C2) is accomplished through Cobalt Strike and Sliver, while Lazagne and Mimikatz are used for credential theft. The attacks also use custom PowerShell and Windows batch scripts to perform lateral movement, privilege escalation, and disabling security software.
“AvosLocker associates uploaded and used custom web shells to enable network access,” the agencies said. Another new component is an executable named NetMonitor.exe that appears as a network monitoring tool but actually acts as a reverse proxy that allows threat actors to connect to the host from outside the victim’s network.
CISA and the FBI are recommending critical infrastructure organizations to implement the necessary mitigations to reduce the likelihood and impact of AvosLocker ransomware and other ransomware incidents.
This includes adopting application controls, limiting the use of RDP and other remote desktop services, restricting the use of PowerShell, requiring phishing-resistant multi-factor authentication, segmenting the network, keeping all systems up to date, and periodically Includes maintaining offline backups.
The development comes as Mozilla warned of ransomware attacks taking advantage of malware campaigns to trick users into installing Trojan versions of Thunderbird, ultimately leading to the deployment of file-encrypting malware and commodity malware families like IcedID.
Ransomware attacks in 2023 have witnessed a major surge, even as threat actors are moving swiftly to deploy ransomware within one day of initial access in more than 50% of engagements, according to Secureworks, dropping from the previous median dwell time of 4.5 days in 2022.
What’s more, in more than 10 percent of the incidents, the ransomware was deployed within five hours.
“The reduction in average residence time is likely due to cyber criminals’ desire to have a lower probability of detection,” said Don Smith, vice president of threat intelligence at the SecureWorks Counter Threat Unit.
“As a result, threat actors are focusing on simple and quick implementations rather than large, multi-site enterprise-wide encryption incidents that are significantly more complex. But the risk from those attacks is still high.”
Exploitation of public facing applications, stolen credentials, off-the-shelf malware, and external remote services have emerged as the three largest initial access vectors for ransomware attacks.
To add insult to injury, the RaaS model and the ready availability of leaked ransomware code has lowered the barrier to entry even for novice criminals, making it an attractive opportunity to make illicit profits.
“While we still see familiar names as the most active threat actors, the emergence of many new and very active threat groups is driving a significant increase in victims and data leaks,” Smith said. “Despite high-profile takedowns and sanctions, cybercriminals are masters of adaptation, and so the threat continues to grow.”
Microsoft said in its annual Digital Defense Report that 70% of organizations facing human-driven ransomware had fewer than 500 employees, and 80 to 90 percent of all compromises originate from unmanaged devices.
Telemetry data collected by the company shows that human-driven ransomware attacks have increased by more than 200 percent since September 2022. Magniber, Lockbit, Hive, and Blackcat comprised about 65 percent of all ransomware encounters.
Additionally, approximately 16 percent of recent successful human-driven ransomware attacks included both encryption and exfiltration, while 13 percent used only exfiltration.
“Ransomware operators are increasingly exploiting vulnerabilities in less common software, making their attacks more difficult to predict and defend against,” the tech giant said. “This reinforces the importance of a holistic security approach.”
Redmond said it saw a “sharp increase” in the use of remote encryption during human-driven ransomware attacks, up an average of 60 percent compared to last year.
“Instead of deploying malicious files on the victim device, encryption is performed remotely, with the system process performing the encryption, rendering process-based remediation ineffective,” Microsoft explained. “This is a sign that attackers are evolving to further reduce their footprint.”
