Cybersecurity researchers have identified a “lightweight way” called iShutdown to reliably identify signs of spyware on Apple iOS devices, including notorious threats like NSO Group’s Pegasus, QuaDream’s Reign, and Intellexa’s Predator.
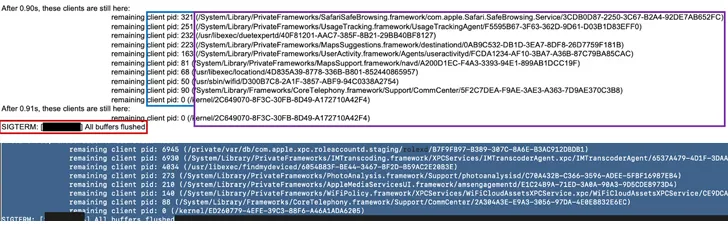
Kaspersky, which analyzed a set of iPhones that were compromised with Pegasus, said the infections left traces in a file named “Shutdown.log,” a text-based system log file available on all iOS devices and which records every reboot event alongside its environment. characteristics.
Security researcher Maher Yamout said, “Compared to more time-consuming acquisition methods like forensic device imaging or full iOS backups, recovering the shutdown.log file is quite simple.” “The log file is stored in a sysdiagnose (sysdiag) archive.”
The Russian cybersecurity firm said it identified entries in the log file that recorded instances where “sticky” processes, such as those associated with the spyware, caused a reboot delay, in some cases observing Pegasus-related processes in over four reboot delay notices.
What’s more, the investigation revealed a presence of a similar filesystem path that’s used by all the three spyware families – “/private/var/db/” for Pegasus and Reign, and “/private/var/tmp/” for Predator – thereby acting as an indicator of compromise.
As noted, the success of this approach depends on ensuring that the targeted user reboots their device as often as possible, the frequency of which varies according to their threat profile.
Kaspersky has also published a collection of Python scripts to extract, analyze, and parse shutdown.log to extract reboot statistics.
“The lightweight nature of this method makes it readily available and accessible,” Yamout said. “In addition, this log file can store entries for many years, making it a valuable forensic artifact for analyzing and identifying unusual log entries.”
This revelation comes as SentinelOne revealed that information stealers targeting macOS like KeySteal, Atomic and JaskaGo (aka CherryPie or Gary Stealer) are increasingly adopting a way to bypass Apple’s built-in antivirus technology called XProtect.
“Despite concerted efforts by Apple to update its XProtect signature database, these rapidly evolving malware strains continue to survive,” said security researcher Phil Stokes. “Relying solely on signature-based detection is insufficient as threat actors have the means and objectives to adapt at speed.”
