Threat actors have been seen targeting semiconductor companies in East Asia by posing as Taiwan Semiconductor Manufacturing Company (TSMC) with lures designed to deliver Cobalt Strike beacons.
The intrusion set, according to EclecticIQ, takes advantage of a backdoor called HyperBro, which is then used as a conduit to deploy commercial attack simulation software and post-exploitation toolkits.
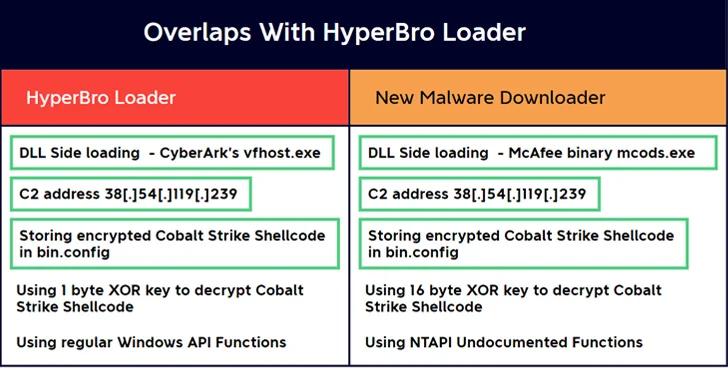
A previously unknown malware downloader is said to have been used to deploy Cobalt Strike in an alternative attack sequence, indicating that threat actors have devised multiple approaches to infiltrate targets of interest.
The Dutch cybersecurity firm attributed the campaign to the use of HyperBro, a threat actor linked to China, which has been used almost exclusively by a threat actor called Lucky Mouse (aka APT27, Budworm, and Emissary Panda).
Tactical overlap has also been detected between the rival behind the attacks and another cluster tracked by RecordedFuture under the name Redhotel, which also overlaps with a hacking crew called Earth Lusca.
Another Chinese connection comes from the use of a potentially compromised Cobra DocGuard web server to host second-stage binaries, including a Go-based implant called ChargeWeapon, for distribution via downloaders.
“ChargeWeapon is designed to gain remote access and send device and network information from infected hosts to attacker-controlled [command-and-control] servers,” EclecticIQ researcher Arda Buyukkaya said in a Thursday analysis.
It’s worth noting that a Trojan version of ESafeNet’s Cobra DocGuard encryption software has also been linked to PlugX’s deployment, with Symantec linking it to a suspected China-Nexus actor codenamed Carderbee.
In the attack series documented by EclecticIQ, a TSMC-themed PDF document is displayed as a decoy after the execution of HyperBro, indicating the use of social engineering techniques to activate the infection.
“By presenting a normal-looking PDF while secretly running malware in the background, the victim is less likely to become suspicious,” Büyükkaya explained.
One notable aspect of the attack is that the hard-coded C2 server address in the Cobalt Strike beacon is disguised as a legitimate jQuery CDN in an attempt to bypass firewall protection.
The disclosure comes as the Financial Times reported that Belgium’s intelligence and security agency, the State Security Service (VSSE), is working to “detect and fight against possible spying and/or interference activities carried out by Chinese entities including Alibaba” at the country’s Liège cargo airport.
Alibaba has denied any wrongdoing.
“China’s activities in Belgium are not limited to the classic spy stealing state secrets or a hacker paralyzing an essential industry or government department from behind his PC,” the agency said in an intelligence report. “In an attempt to influence decision-making processes, China uses a variety of state and non-state resources.”
A report released last month by the US Department of Defense (DOD) described China as a “widespread and pervasive cyber espionage threat” and said it steals technology secrets and conducts surveillance efforts to gain strategic advantage.
“Using cyber means, the PRC has engaged in prolonged campaigns of espionage, evasion, and compromise against key defense networks and broader U.S. critical infrastructure, particularly the Defense Industrial Base (DIB),” the DOD said.
