Two different North Korean nation-state actors have been linked to cyber intrusions against NPO Mashinostroyeniya, a major Russian missile engineering company.
Cyber security firm SentinelOne said it has identified “two examples of North Korea-related compromises of sensitive internal IT infrastructure”, including an email server compromise and the deployment of a Windows backdoor called OpenCarrot.
ScarCruft has been held responsible for the breach of Linux email servers. On the other hand, OpenCarrot is a known implant that was first identified as being in use by the Lazarus group. The attacks were marked in mid-May 2022.
NPO Mashinostroyeniya, a rocket design bureau based in Reutov, was sanctioned by the US Treasury Department in July 2014 in connection with “Russia’s continued efforts to destabilize eastern Ukraine and its ongoing annexation of Crimea”.
While both ScarCruft (aka APT37) and Lazarus Group are affiliated with North Korea, it is worth noting that the former is overseen by the Ministry of State Security (MSS). Lazarus Group is part of Lab 110, a component of the Reconnaissance General Bureau (RGB), the country’s primary foreign intelligence service.
The development marks a rare convergence where two independent threat activity groups based in North Korea have targeted the same entity, indicating a “highly desirable strategic espionage mission” that could benefit its controversial missile program.
OpenCarrot is implemented as a Windows dynamic-link library (DLL) and supports over 25 commands for performing reconnaissance, manipulating file systems and processes, and managing multiple communication mechanisms.
“With a wide range of supported functionality, OpenCarrot enables full agreement of infected machines as well as coordination of multiple infections across a local network,” said security researchers Tom Hegel and Aleksandar Milenkoski.
The exact method used to break the attack chain employed to distribute OpenCarrot along with email servers remains unknown, although ScarCruft has been known to rely on social engineering to phish victims and deliver backdoors such as RokRat.
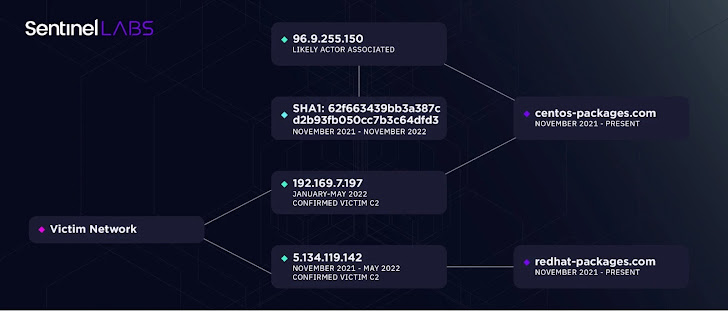
In addition, closer inspection of the attack infrastructure revealed two domains, centos-package[.]com and redhat-package[.]com, which are similar to the names of the threat actors used in the JumpCloud hack in June 2023.
The researchers said, “This incident is a striking example of North Korea’s active measures to covertly advance their missile development objectives, as evidenced by their direct agreements with the Russian Defense-Industrial Base (DIB) Organization.” “
