A malicious toolset called SpaceColon is being deployed as part of an ongoing campaign to spread a variant of the Scarab ransomware to victim organizations globally.
“It likely found its way into victim organizations by compromising vulnerable web servers either by their operators or via RDP credentials,” ESET security researcher Jakub Souček said in a detailed technical article published Tuesday.
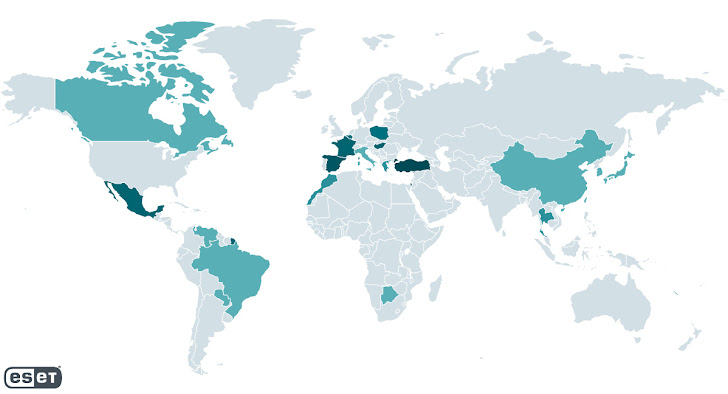
The Slovak cyber security firm, which dubbed the threat actor CosmicBeetle, said Spacecolon originated in May 2020. The highest numbers of victims have been found in France, Mexico, Poland, Slovakia, Spain and Turkey.
Although the exact origins of Paragon are unclear, several Spacecolon variants are said to contain Turkish strings, possibly pointing to the involvement of a Turkish-speaking developer. There is currently no evidence linking it to any other known threat actor group.
Some of the targets include a hospital and a tourist resort in Thailand, an insurance company in Israel, a local government institution in Poland, an entertainment provider in Brazil, an environmental company in Turkey, and a school in Mexico.
Souček explained, “CosmicBeetle does not choose its targets; rather, it finds servers that do not have critical security updates and exploits this to its advantage.”
It’s worth noting that SpaceColon was first documented by Polish company Zaufana Trzecia Strona as early as February 2023, which may have prompted a rival to make changes to its arsenal in response to the public disclosure.
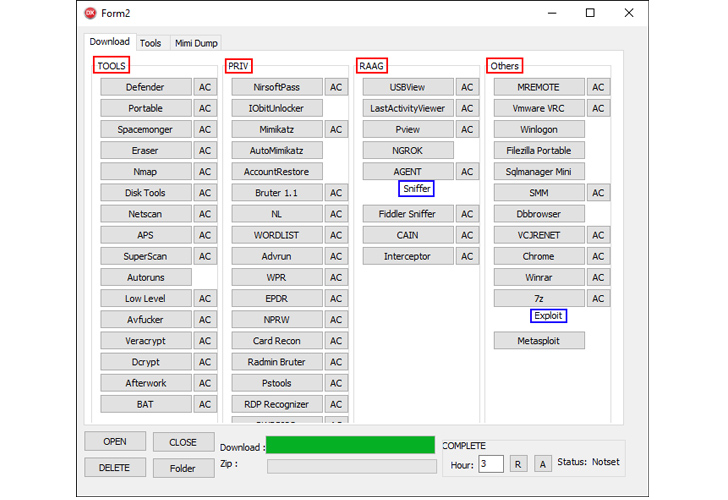
The primary component of Spacecolon is ScHackTool, a Delhi-based orchestrator that’s used to deploy an installer, which, as the name implies, installs ScService, a backdoor with features to execute custom commands, download and execute payloads, and retrieve system information from compromised machines.
ScHackTool also serves as a conduit for installing a wide range of third-party tools sourced from a remote server (193.149.185[.]23). The ultimate goal of the attacks is to take advantage of the access provided by ScService to distribute a variant of the Scarab ransomware.
An alternate version of the infection chain identified by ESET involves the use of Impacket to deploy ScService as opposed to the use of ScHackTool, indicating that threat actors are experimenting with different approaches.
CosmicBeetle’s financial motives are further bolstered by the fact that the ransomware payload also drops a Clipper malware designed to monitor the system clipboard and modify cryptocurrency wallet addresses under the attacker’s control.
Furthermore, there is evidence that the adversary is actively developing a new ransomware strain dubbed ScRansom, which attempts to encrypt all hard, removable, and remote drives using the AES-128 algorithm with a key generated from a hard-coded string.
“CosmicBeetle doesn’t make much effort to hide its malware and leaves a lot of artifacts on compromised systems,” Souček said. “Little or no anti-analysis or anti-emulation techniques are implemented. ScHackTool relies heavily on its GUI, but, at the same time, has many non-functional buttons.”
“CosmicBeetle operators use ScHackTool primarily to download additional tools of choice to affected machines and run them as needed.”
