New findings from Group-IB suggest that a recently patched security flaw in the popular WinRAR archive software is being used as a zero-day since April 2023.
The vulnerability, cataloged as CVE-2023-38831, allows threat actors to spoof file extensions, thereby making it possible to launch malicious scripts contained within an archive that masquerades as seemingly innocuous image or text files. It was addressed in version 6.23 released on August 2, 2023, alongside CVE-2023-40477.
In attacks discovered by the Singapore-based firm in July 2023, specially crafted ZIP or RAR archive files distributed via trading-related forums such as Forex Station have been used to deliver a variety of malware families such as DarkMe, GuLoader, and Remcos RAT.
“After infecting the device, cyber criminals withdraw money from broker accounts,” said Group-IB malware analyst Andrey Polovinkin. Equipment of 130 traders have been tampered with under the campaign. The total number of victims and the financial loss caused by this activity is currently unclear.
The booby-trapped archive file is created such that it contains an image file as well as a folder with the same name.
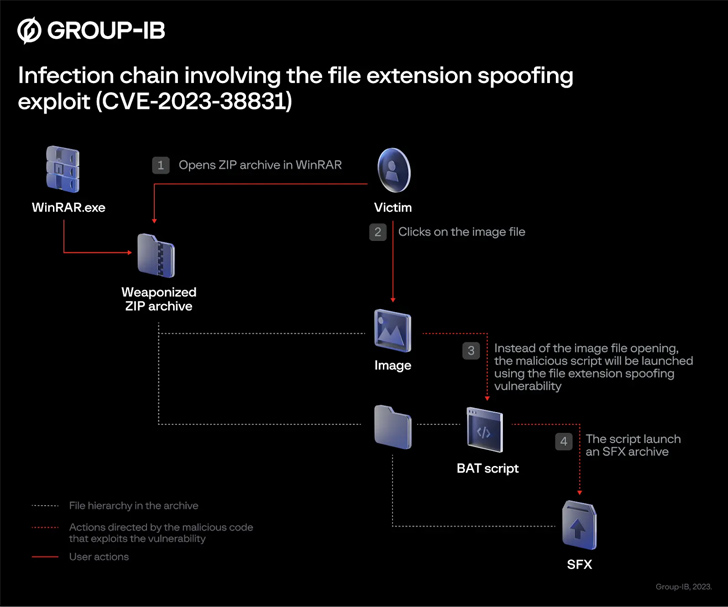
As a result, when a victim clicks on the image, a batch script contained within the folder is executed, which is used to launch the next step, an SFX CAB archive designed to extract and launch additional files. Furthermore, the script loads a fake image so as not to arouse suspicion.
“CVE-2023-38831 is caused by a processing error opening a file in a zip archive,” Polovinkin told. “The weaponized Zip archiver has been distributed across at least 8 popular trading platforms, so the geographic location of victims is widespread, and the attacks are not targeted to specific countries or industries.”
It is not yet known who is behind the attacks by exploiting the WinRAR vulnerability. As mentioned, DarkMe is a Visual Basic Trojan attributed to the Evilnum group, first documented by NSFOCUS in September 2022 in connection with a phishing campaign codenamed DarkCasino targeting European online gambling and trading services.
A malware strain called GuLoador (aka CloudEye) is also distributed using this method which then attempts to fetch the Remcos RAT from a remote server.
“The recent cases of the CVE-2023-38831 exploit remind us of the continuing risks associated with software vulnerabilities,” said Polovinkin. “Threat actors are highly resourceful, and they will always find new ways to find vulnerabilities and then exploit them.”
