A new variant of the Apple macOS malware XLoader has surfaced, hiding its malicious features under the guise of an office productivity app called “OfficeNote”.
“The new version of XLoader is bundled inside a standard Apple disk image with the name OfficeNote.dmg,” SentinelOne security researchers Dinesh Devadoss and Phil Stokes said in Monday’s analysis. “The application contained within is signed with the developer signature MAIT JAKHU (54YDV8NU9C).”
XLoader, first discovered in 2020, is considered the successor to Formbook and is an information stealer and keylogger offered under the Malware-as-a-Service (MaaS) model. A macOS version of the malware surfaced in July 2021, distributed as a Java program in the form of a compiled .JAR file.
“Such files require the Java Runtime Environment, and for this reason a malicious .jar file will not execute on an out-of-the-box macOS install, since Apple stopped shipping the JRE with the Mac over a decade ago,” The Cyber security firm noted at the time.
The latest version of XLoader on July 17, 2023 overcame this limitation by switching to programming languages such as C and Objective C with signing of disk image files. Apple has since disowned the signing.
SentinelOne said it detected multiple builds of the artifact on VirusTotal throughout the month of July 2023, indicating a widespread campaign.
“Advertisements on crimeware forums offer to rent the Mac version for $199/month or $299/3 months,” the researchers said. “Interestingly, it is relatively expensive compared to the Windows variants of XLoader, which cost $59/month and $129/3 months.”
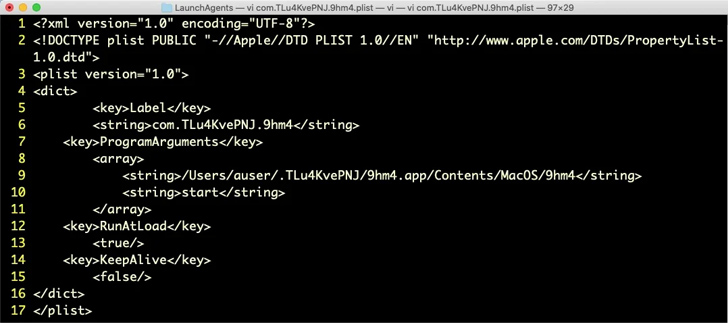
Once executed, OfficeNote throws an error message saying that it “could not be opened because the parent item could not be found”, but, in fact, it installs a launch agent in the background for persistence.
XLoader is designed to collect clipboard data as well as information stored in directories associated with web browsers such as Google Chrome and Mozilla Firefox. However, Safari is not targeted.
In addition to taking steps to avoid analysis manually and by automated solutions, the malware is configured to run sleep commands to delay its execution and avoid raising any red flags.
The researchers concluded, “XLoader remains a threat to macOS users and businesses.”
“This latest iteration masquerading as an office productivity application shows that the targets of interest are clearly users in a working environment. The malware attempts to steal browser and clipboard secrets that could be used or sold to other threat actors for further compromise.”
