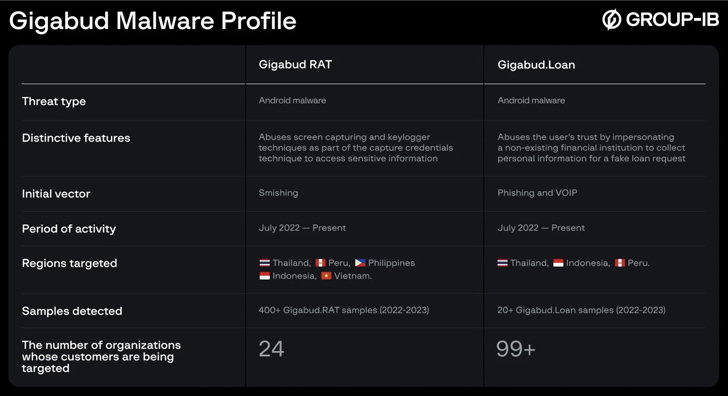
Account holders of multiple financial institutions in Thailand, Indonesia, Vietnam, Philippines and Peru are being targeted by Android banking malware called Gigabud RAT.
“One of the unique features of the Gigabud RAT is that it does not perform any malicious action unless the user is authorized by a fraudster in a malicious application, […] making it harder to detect.” Said Group-IB researchers Pavel Naumov and Artem Grishchenko.
“Instead of using HTML overlay attacks, the Gigabud RAT collects sensitive information primarily through screen recording.”
The Gigabud RAT was first documented by Cyble in January 2023, when it was observed impersonating bank and government apps to steal sensitive data. It is known to have been active in the wild since at least July 2022.
The Singapore-based company said it has also identified a second variant of the malware, except for one with RAT capabilities. Named Gigabud.loan, it comes in the guise of a loan application that is capable of spitting out user-inputted data.
“The targets were people who were lured into filling out bank card application forms in order to obtain loans at low interest,” the researchers said. “Victims are convinced to provide personal information during the application process.”
Both malware variants spread via phishing websites, whose links are sent to victims via SMS or instant messages on social media networks. Gigabud.Loan is also distributed directly as APK files sent via messages on WhatsApp.
Targets who are contacted on social media are often coerced into visiting the sites on the pretext of completing tax audits and claiming refunds.
While Android devices have the “install from unknown sources” setting disabled by default as a security measure to prevent the installation of apps from untrusted sources, the operating system allows other apps on the device, such as web browsers, email clients, file allows to install. Managers and messaging apps need to request the “REQUEST_INSTALL_PACKAGES” permission.
Should a user allow such apps, it allows threat actors to install fake APK files, bypassing the “Install from unknown sources” option.
Gigabud acts similarly to other Android banking trojans by requesting Accessibility Services permission to perform screen capturing and logging keystrokes. It is also equipped to convert bank card numbers to clipboard and make automatic fund transfers through remote access.
On the other hand, Gigabud.Loan functions as a tool to collect personal information such as full name, identity number, national identity document photo, digital signature, education, income info, bank card information, and phone number under the guise of submitting a loan request to the bank.
The findings come after the discovery of 43 fake apps on the Google Play Store that load ads when the device’s screen is off. Apps with cumulative downloads of 2.5 million have been removed or updated by the developers to remove the ad fraud component.
McAfee said the adware, once installed, sought users’ permission to exit apps while saving battery and allowed it to dominate other apps, effectively opening the door to further malicious attacks such as loading ads in the background and displaying phishing pages.
The ad fraud library used by the apps also adopts a delay strategy to avoid detection and can be modified remotely by operators using the Firebase messaging service, adding an additional layer of complexity to it.
The disclosure comes at a time when the US Federal Bureau of Investigation (FBI) is warning of an increase in the number of scammers pretending to be recovery and tracing companies that help victims of cryptocurrency investment scams recover lost assets.
The FBI said, “Recovery scheme fraudsters charge upfront fees and after receiving the initial deposit either cease communication with the victim or present incomplete or inaccurate tracing reports and request additional fees to recover funds.”
In addition, the agency cautioned that cyber criminals masquerading as mobile beta-testing apps masquerading as legitimate cryptocurrency investment apps to defraud potential victims by facilitating the theft of personally identifiable information (PII) and financial account data have been embedding code.
“Using names, images or descriptions similar to popular apps can make apps appear legitimate,” the agency explained. “Cyber criminals often use phishing or romance scams to establish communication with a victim, then direct the victim to download a mobile beta-testing app located in a mobile beta-testing app environment, and make large financial payments.”
In these schemes, threat actors contact potential victims on dating and social networking apps and build trust with the ultimate goal of enticing them to download pre-release versions of the apps.
“Victims enter valid account details into the app, send money they believe will be invested in cryptocurrency, but instead the victim’s money is sent to cyber criminals,” the FBI said.
It is worth noting that the misuse of Apple’s TestFlight beta testing framework to perpetrate the pig slaughter scam was exposed by cyber security firm Sophos last year.
Recent waves of campaigns, also known as cryptoroms, have weaponized Apple’s enterprise and developer ad-hoc app distribution schemes to distribute fake crypto apps that circumvent restrictions that allow users to download iOS apps outside the App Store.
In other instances, a seemingly innocuous app is trojanized after being approved and published on the Apple and Google app storefronts by altering remote code to point to an attacker-controlled server to introduce malicious behavior.
