Cybersecurity researchers have discovered a Python variant of NodeStealer, a stealthy malware perfectly equipped to capture Facebook business accounts as well as cryptocurrencies.
Palo Alto Networks’ Unit 42 said it detected a previously undocumented strain as part of an operation that began in December 2022. There is no evidence to suggest that any cyber offensive is currently active.
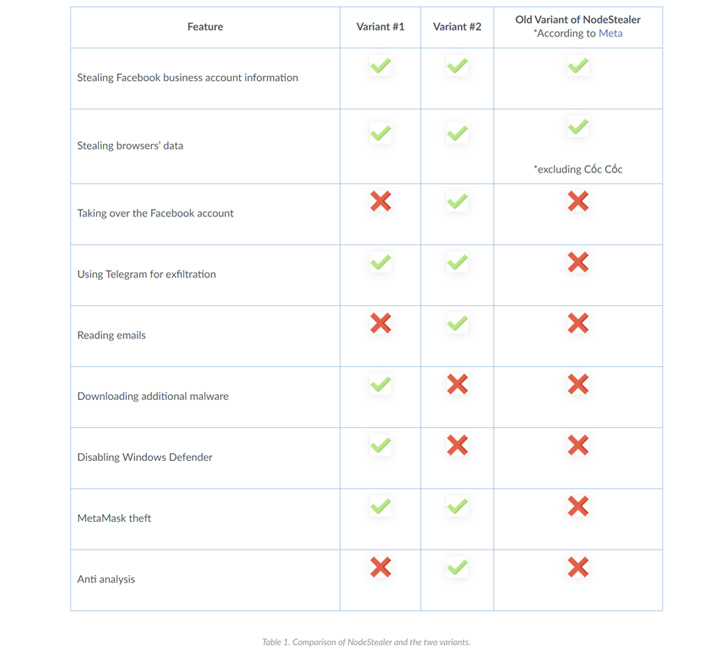
NodeStealer was first exposed by Meta in May 2023, in which it was described as a stealer capable of stealing cookies and passwords from web browsers to compromise Facebook, Gmail and Outlook accounts. While previous samples were written in JavaScript, the latest versions are coded in Python.
“NodeStealer poses a huge risk to both individuals and organizations,” said Unit 42 researcher Lior Rochberger. “Apart from the direct impact on Facebook business accounts, which is primarily financial, the malware also steals credentials from browsers, which can be used for further attacks.”
The attacks begin with fake messages on Facebook that purportedly claim to offer free “professional” budget tracking Microsoft Excel and Google Sheets templates, tricking victims into downloading a zip archive file hosted on Google Drive.
The ZIP file embeds within it the stealer executable that, besides capturing Facebook business account information, is designed to download additional malware such as BitRAT and XWorm in the form of ZIP files, disable Microsoft Defender Antivirus, and carry out crypto theft by using MetaMask credentials from Google Chrome, Cốc Cốc, and Brave web browsers.
The download is accomplished through a User Account Control (UAC) bypass technique that employs fodhelper.exe to execute PowerShell scripts that retrieve ZIP files from remote servers.
It is worth noting that the FodeHelper UAC bypass method has also been adopted by the financially motivated threat actors behind the Casabaneiro banking malware to gain elevated privileges on infected hosts.
Unit 42 said it also spotted an advanced Python version of NodeStealer that steals credentials and crypto by implementing anti-analysis features, parsing emails from Microsoft Outlook, and even attempting to take over an associated Facebook account.
Once the necessary information is gathered, the files are extracted through the Telegram API, after which they are mechanized to erase the traces.
NodeStealer also links to malware such as Ducktail, part of a growing trend of Vietnamese threat actors trying to break into Facebook business accounts to commit ad fraud and spread malware among other users on the social media platform.
The development comes as threat actors have been observed taking advantage of WebDAV servers to deploy BATLOADER, which is used to distribute XWorm as part of a multi-stage phishing attack.
“Facebook business account owners are encouraged to use strong passwords and enable multi-factor authentication,” Rochberger said. “Take the time to provide your organization with education on phishing tactics, especially modern, targeted approaches that impact current events, business needs, and other engaging topics.”
