Rival Russa-Nexus has been linked to 94 new domains, indicating that the group is actively modifying its infrastructure in response to public disclosures about its activities.
Cyber security firm Recorded Future has linked the new infrastructure tracking to a threat actor known as Blue Charlie, a hacking crew loosely linked to Blue Callisto, Callisto (or Callisto), Coldriver, Star Blizzard (formerly Seaborgium) and Known by the names TA446. Blue Charlie was previously given the temporary designation Threat Activity Group 53 (TAG-53).
“These changes demonstrate that these threat actors are aware of industry reporting and have taken a certain level of caution in their efforts to obscure or modify their activity with the aim of obfuscating security researchers,” the company said in a new technical report.
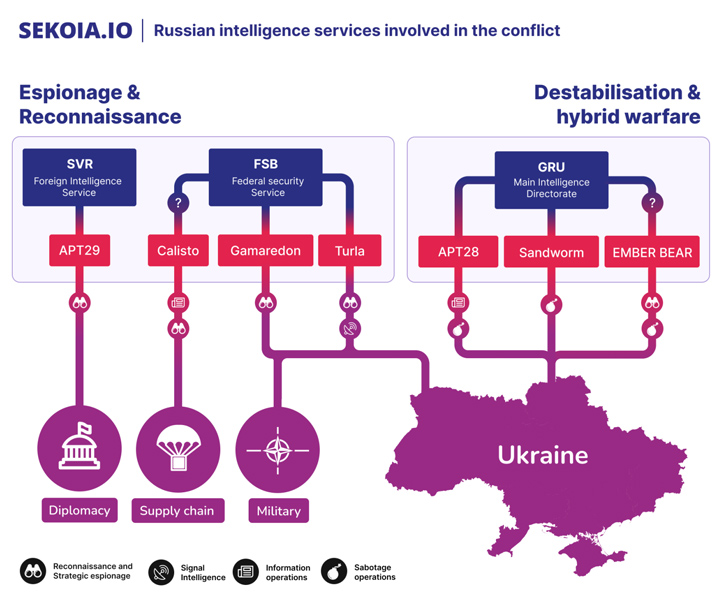
BlueCharlie is believed to be affiliated with Russia’s Federal Security Service (FSB), and the threat actor engaged in phishing campaigns aimed at domains targeting private sector companies, nuclear research laboratories, and non-governmental organizations. Stealing credentials using Appear as login page of government organizations, Ukraine in crisis relief. It is said to have been active since at least 2017.
“Callisto collection activities may contribute to Russian efforts to disrupt the Kiev supply-chain for military reinforcements,” Sequoia said earlier this year. “In addition, Russian intelligence collection regarding evidence related to identified war crimes may be conducted in order to anticipate future accusations and create a counter-narrative.”
Another report published by NISOS in January 2023 identified possible connections between the group’s attack infrastructure and a Russian company that had contracts with government entities in the country.
Recorded Future said, “BlueCharlie has conducted persistent phishing and credential theft campaigns that further enable intrusions and data theft.” He said the actor conducts extensive reconnaissance to increase the chances of success of his attacks.
The latest findings suggest that BlueCharlie has moved to a new naming pattern for its domains, which includes keywords related to information technology and cryptocurrency, such as cloudrootstorage[.]com, directexpressgateway[.]com, storagecryptogate[.] ]com, and pdfsexcloudroute[.]com.
Of the 94 new domains, 78 are said to have been registered using NameCheap. Some other domain registrars used include Porkbun and Reggae.
To mitigate the threats posed by state-sponsored advanced persistent threat (APT) groups, it is recommended that organizations implement phishing-resistant multi-factor authentication (MFA), disable macros by default in Microsoft Office, And enforce a frequent password reset policy.
“While the group uses relatively common techniques to carry out attacks (such as the use of phishing and a historical reliance on open-source offensive security tools), its continued use of these methods, determined posture and progressive evolution of tactics have deterred the group.” “It remains formidable and capable,” said the company.
