IcedID, also known as Bokbot, is a variant of malware similar to Emotet and Qakbot that began as a banking Trojan in 2017 before transitioning to the role of early access facilitator for other payloads. Recent versions of the malware have been observed removing functionality related to online banking fraud in order to prioritize ransomware delivery.
The BackConnect (BC) module, first documented by Netresec in October 2022, relies on a proprietary command-and-control (C2) protocol to exchange commands between a server and an infected host. The protocol, which comes with a VNC component for remote access, has also been identified in other malware such as the now-discontinued Bazerloader and QakBot.
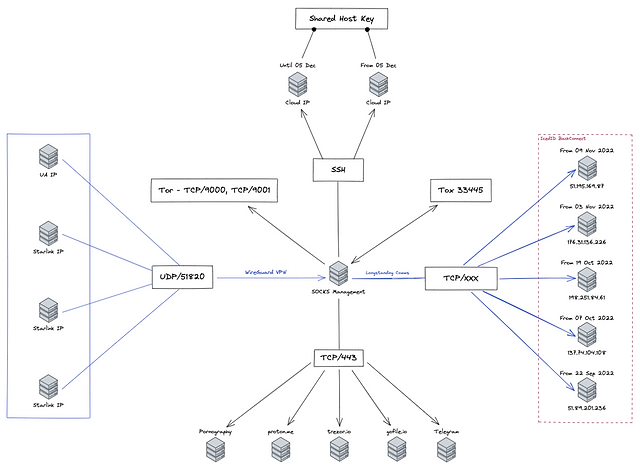
IcedID inside backconnect protocol
In December 2022, Team Cymru reported the discovery of 11 BC C2s active since July 1, 2022, suggesting that operators possibly based in Moldova and Ukraine are overseeing separate elements of the BC protocol.
Palo Alto Networks Unit 42 said in late May 2023, “For the past several months, backconnect traffic caused by IcedID was easy to detect because it occurred on TCP port 8080.” The IcedID has been changed to TCP port 443, making it harder to find.”
The latest analysis of Team Cymru’s attack infrastructure revealed that as the number of BC C2 has increased from 11 to 34 since January 23, 2023, the average uptime of the servers has decreased from 28 days to eight days.
“As of April 11, 2023, a total of 20 high-trust BC C2 servers were identified based on the management infrastructure,” the cyber security firm said in a report shared.
“The first observation is that there has been an increase in the number of concurrent C2 servers in operation […], with four C2 servers receiving management communications on a particular day.”
A further investigation into traffic originating from BC C2 servers revealed eight victims between late April 2023 and June 2023 who “communicated with three or more BC C2 servers over a relatively long period of time.”
Based on the amount of traffic observed between the victims and the servers, it is also suspected that the same IceID operator or associate is reaching multiple victims within the same time frame.
“In examining the management infrastructure associated with IcedID BC, we have been able to discern a number of different access patterns from users who we estimate are both involved with the day-to-day operations of IcedID, and their partners who interact with victims and hosts after the agreement,” Team Simru said.
“Evidence in our NetFlow data suggests that some isID victims are used as proxies in spamming operations enabled by BC’s SOCKS capabilities. This is a potential double whammy for victims, not only were they compromised and suffered data/financial loss, but they were used for purposes of further proliferating IcedID campaigns.”
