A high-severe security flaw has been disclosed in the Python URL parsing function that can be used to bypass domain or protocol filtering methods implemented with blocklists, ultimately resulting in arbitrary file reads and command execution.
The CERT Coordination Center (CERT/CC) said in Friday’s advisory, “URLParse have a parsing problem when the entire URL begins with empty characters.” “This issue affects the parsing of both the hostname and the scheme, and will eventually cause any blocklisting method to fail.”
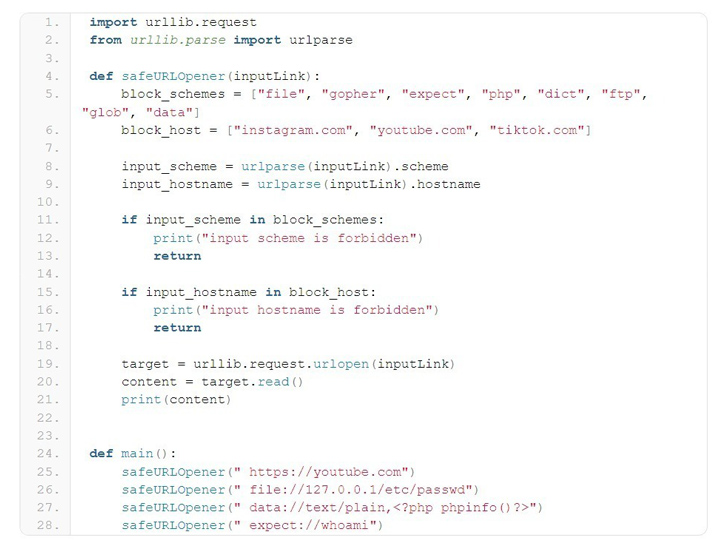
The flaw has been assigned the identifier CVE-2023-24329 and has a CVSS score of 7.5. Security researcher Yebo Cao is credited with discovering and reporting the issue in August 2022. This has been addressed in the following versions –
- >= 3.12
- 3.11.x >= 3.11.4
- 3.10.x >= 3.10.12
- 3.9.x >= 3.9.17
- 3.8.x >= 3.8.17, and
- 3.7.x >= 3.7.17
urllib.parse is a widely used parsing function that makes it possible to split a URL into its components or, alternatively, to combine the components into a URL string.
CVE-2023-24329 arises as a result of a lack of input validation, thus leading to a scenario where it is possible to bypass blocklisting methods by supplying URLs starting with empty characters (for example, ” https://youtube[.] com”).
“Although blocklists are considered an inferior choice, there are many scenarios where blocklists are still needed,” Cao said. “This vulnerability would allow an attacker to bypass developer-defined protections for the scheme and host. This vulnerability can be expected to support SSRF and RCE in a wide range of scenarios.”
The revelation comes as new research has found that security fixes in Python are often done through “silent” code commits, without an associated Common Vulnerabilities and Exposures (CVE) identifier, thus allowing malicious actors this gives them the opportunity to potentially exploit unknown vulnerabilities in unpatched systems.
