Cybersecurity experts have discovered another Malware-as-a-Service (MaaS) threat called BunnyLoader that is being advertised for sale on Cybercrime Underground.
“BunnyLoader provides various functionalities such as downloading and executing second-stage payloads, stealing browser credentials and system information, and more,” Zscaler ThreatLabz researchers Neeraj Shivtarkar and Satyam Singh said in an analysis published last week.
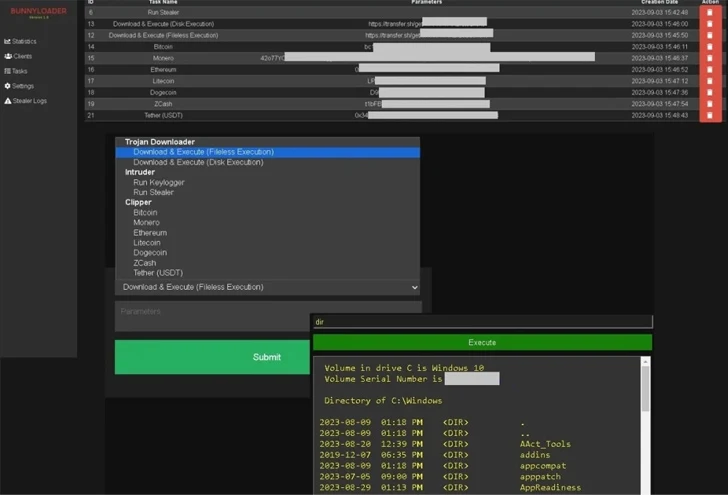
Its other capabilities include running remote commands on the infected machine, a keylogger to capture keystrokes, and a clipper functionality to monitor the victim’s clipboard and replace content matching cryptocurrency wallet addresses with actor-controlled addresses.
A C/C++-based loader is offered for $250 for a lifetime license, the malware is said to be under continuous development since its launch on September 4, 2023, with new features and enhancements including anti-sandbox and Contains antivirus evasion techniques.
As part of updates released on September 15 and September 27, 2023, “critical” SQL injection flaws were also fixed in the command-and-control (C2) as well as the C2 panel, which would have provided access to the database.
According to author PLAYER_BUNNY (aka PLAYER_BL), a major selling point of BunnyLoader is its fileless loading feature which “makes it difficult for antivirus to remove attackers’ malware.”
C2 Panel offers buyers options to monitor active tasks, infection statistics, total number of connected and inactive hosts, and piracy logs. It also provides the ability to scrape information and remotely control damaged machines.
The exact early access mechanism used to distribute BunnyLoader is currently unclear. Once installed, the malware establishes persistence through Windows registry changes and executes a series of sandbox and virtual machine checks before activating its malicious behavior by sending task requests to remote servers and receiving desired responses.
This includes Trojan downloaders to download and execute next-stage malware, intruders to run keyloggers and stealers to collect data from messaging apps, VPN clients, and web browsers, and to redirect cryptocurrency payments and profit from illicit transactions.
The final step involves compressing all the collected data into a zip archive and transmitting it to the server.
“Bunnyloader is a new MaaS threat that is constantly evolving its tactics and adding new features to conduct successful campaigns against its targets,” the researchers said.
These findings follow the discovery of another Windows-based loader called MidgeDropper that is likely distributed via phishing emails to deliver anonymous second-stage payloads from a remote server.
The development also comes amid the introduction of two new information-stealing malware strains named Agniane Stealer and The-Murk-Stealer, which support the theft of a wide range of information from breached endpoints.
While Agniane Stealer is available as a $50 monthly subscription, the latter is reportedly available on GitHub for educational purposes, making it suitable for abuse by other threat actors. Some other stealers hosted on GitHub include Stealerium, Impost3r, blank-grabber, nivistealer, creal-stealer, and cstealer.
Cyfirma said, “While claiming that the tool is for educational purposes, the author’s contradiction arises when urging not to upload the final binary to platforms such as VirusTotal (VT), where the antivirus solution uses its signature.”
It is not just new malware services, but cyber criminals are also enhancing the features of existing MaaS platforms with updated attack chains to avoid detection by security tools. It includes a version of Redline Stealer that uses Windows batch scripts to launch malware.
“[Redline Stealer] is being distributed through a variety of mediums and threat actors are constantly changing techniques to remain undetected for longer periods of time,” the cybersecurity firm said. “It is also being sold on underground platforms and encouraging cyber criminals to carry out their evil intentions.”
