Cyber security firm Check Point said the activity, dubbed SmogX, has been ongoing since at least December 2022, part of a wider trend of Chinese adversaries turning their attention to Europe.
Check Point said, “The campaign uses new delivery methods to deploy a new variant of PlugX (specifically – HTML smuggling), an implant commonly associated with a variety of Chinese threat actors. “
“Although the payload itself remains very similar to that found in the older PlugX variant, its delivery methods result in a lower detection rate, which helped the campaign fly under the radar until recently.”
The exact identity of the threat actor behind the operation is a bit hazy, though existing clues point to Mustang Panda, which also shares overlap with tracked groups such as Earth Prieta, RedDelta, and Check Point’s own designation Camaro Dragon.
However, the company said there is “insufficient evidence” at this stage to conclusively attribute it to adverse collective action.
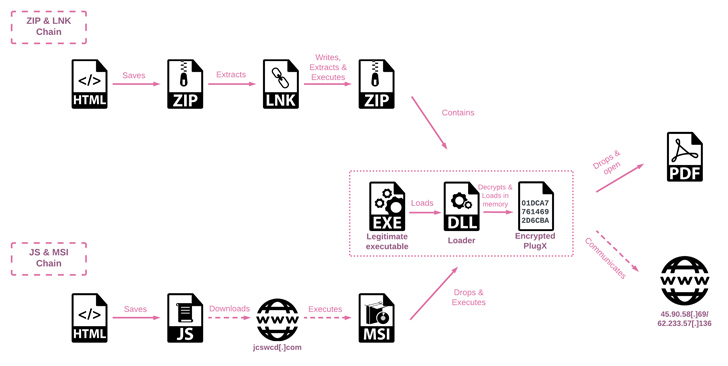
The latest attack sequence is critical of the use of HTML smuggling – a stealth technique in which legitimate HTML5 and JavaScript features are misused to assemble and launch malware – in fake documents attached to spear-phishing emails.
As Trustwave noted earlier this February, “HTML Smuggling employs HTML5 features that can work offline by storing the binary in an immutable blob of data within the JavaScript code.” “The data blob, or embedded payload, is decoded into a File object when opened via a web browser.”
Analysis of the documents uploaded to the VirusTotal malware database suggests they are designed to target diplomats and government entities in Czechia, Hungary, Slovakia, the U.K., Ukraine, and possibly France and Sweden.
In one instance, the threat actor is said to have employed a Uyghur-themed lure (“China tries to block prominent Uyghur speaker at UN.docx”) that, when opened, displayed an embedded, invisible Tracking signals through to an external server. Pixel to spit out reconnaissance data.
The multi-stage infection process uses DLL side-loading methods to decrypt and launch the final payload, PlugX.
Also called CorePlug, this malware dates back to 2008 and is a modular Trojan capable of accommodating “various plugins with different functionality” that enable operators to perform file theft, screen capture, keystroke logging, and command execution.
“During the course of our samples investigation, the threat actor sent a batch script sent from C&C servers, intended to erase any trace of their activities,” Check Point said.
“This script, named del_robotask update.bat, deletes valid executables, PlugX loader DLLs and registry keys implemented for persistence, and eventually removes itself. It is likely that it is detected by threat actors.” resulted in them being under investigation.”
