New findings suggest that a new vulnerability disclosed in GitHub could put thousands of repositories at risk for repojacking attacks.
“This flaw could allow an attacker to exploit race conditions within GitHub’s repository creation and username renaming operations,” Checkmark security researcher Elad Rapoport said in a technical report shared.
“The successful exploitation of this vulnerability impacted the open-source community by enabling the hijacking of over 4,000 code packages in languages such as Go, PHP, and Swift, as well as GitHub Actions.”
Following responsible disclosure on March 1, 2023, the Microsoft-owned code hosting platform has resolved the issue as of September 1, 2023.
Repojacking, short for repository hijacking, is a technique where a threat actor is able to bypass the popular security mechanism called repository namespace retirement and ultimately take control of the repository.
What the security measure does is prevent other users from creating a repository with the same name as the repository containing more than 100 clones when the user account is renamed. In other words, the combination of username and repository name is considered “retired”.
Should this protection be trivially circumvented, it could enable threat actors to create new accounts with the same username and upload malicious repositories, potentially leading to attacks on the software supply chain.
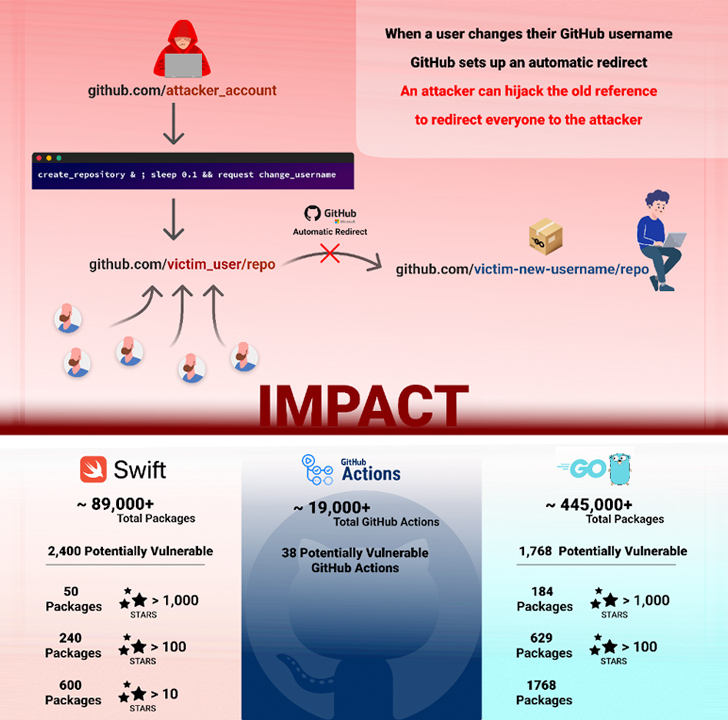
The new method mentioned by Checkmarks takes advantage of a potential race condition between building the repository and renaming the username to get the repository. Specifically, it involves the following steps −
- Victim has namespace “victim_user/repo”
- The victim has changed the name of “victim_user” to “renamed_user”
- The “victim_user/repo” repository is now closed
- A threat actor with the username “attacker_user” simultaneously creates a repository named “repo” and renames the username “attacker_user” to “victim_user”.
The final step is accomplished using API requests for repository creation and named request interception for username changes. The development comes nearly nine months after GitHub fixed a similar bypass flaw that could open the door to relaunching the attacks.
“The discovery of this novel vulnerability in GitHub’s repository creation and username renaming operations underscores the persistent risks associated with the ‘popular repository namespace retirement’ mechanism,” Rapoport said.
