The flaw, tracked as CVE-2023-28121 (CVSS score: 9.8), is a case of authentication bypass that enables unauthenticated attackers to impersonate arbitrary users and perform certain tasks as the impersonated user, including an administrator, that could potentially lead to a site acquisition.
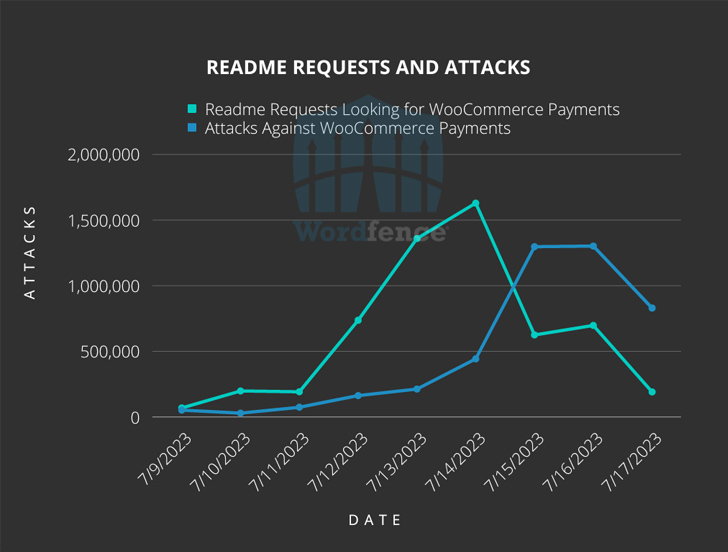
Wordfence security researcher said, “The massive attack against the vulnerability assigned to CVE-2023-28121 began on Thursday, July 14, 2023 and continued through the weekend, hitting 1.3 million against 157,000 sites on Saturday, July 16, 2023 Attacks reached. Ram Gall said in a post on Monday.
Versions of WooCommerce Payments 4.8.0 to 5.6.1 are vulnerable. The plugin is installed on over 600,000 sites. Patches for the bug were released by WooCommerce in March 2023, with WordPress issuing auto-updates to sites using affected versions of the software.
A common denominator seen in attacks insists on the use of the HTTP request header “X-Wcpay-Platform-Checkout-User: 1” which causes vulnerable sites to assume any additional payloads come from an administrative user.
Wordfence said the above flaws are being weaponized to deploy the WP Console plugin, which can be used by an administrator to execute malicious code and install backdoor persistence and file uploaders on a compromised site.
Adobe ColdFusion flaws were exploited in the wild
The disclosure comes after Rapid7 reported that it has observed active exploitation of Adobe ColdFusion vulnerabilities in multiple customer environments since July 13, 2023, to deploy web shells to infected endpoints.
“It appears that threat actors are exploiting CVE-2023-29298 in conjunction with a secondary vulnerability,” said Rapid7 security researcher Caitlin Condon. The additional flaw appears to be CVE-2023-38203 (CVSS score: 9.8), a deserialization flaw that was addressed in an out-of-band update released on July 14.
CVE-2023-29298 (CVSS score: 7.5) is related to an access control bypass vulnerability that affects ColdFusion 2023, ColdFusion 2021 Update 6 and below, and ColdFusion 2018 Update 16 and below.
“This vulnerability allows an attacker to gain access to administration endpoints by inserting an unexpected additional forward slash character into the requested URL,” Rapid7 disclosed last week.
However, Rapid7 warns that the fix for CVE-2023-29298 is incomplete and may be minorly modified to bypass patches released by Adobe.
Users are advised to update to the latest version of Adobe ColdFusion to stay protected against potential threats, as improvements made to resolve CVE-2023-38203 break the exploit chain.
