“This sophisticated campaign uses a Trojan that follows a multi-stage infection chain using specially crafted modules at each stage,” Zsklar researchers Neeraj Shivtarkar and Preet Kamal said in a report published last week.
“These modules are custom designed to carry out malicious activities, such as injecting harmful code into remote processes, bypassing User Account Control via COM elevation monikers, and through clever techniques such as system reboot and parent process checks.”
The six-step effort has all the hallmarks of a well-crafted attack sequence, starting with a phishing email containing an embedded link that evades domain-based detection hosted on an Amazon EC2 instance.
Email messages take advantage of invoice-themed bait to trick unwitting recipients into opening them, thereby activating the infection. Within the zip archive is a downloader executable engineered to establish persistence via the LNK file in the Windows Startup folder and communicate with a remote server to retrieve the six next-stage payloads as MP3 files.
Downloader is also responsible for generating a batch script that restarts the system after a timeout of 10 seconds. “This is done to avoid sandbox detection as malicious activities happen only after reboot,” the researchers said.
The received payload contained “icepdfeditor.exe”, a validly signed binary by ZOHO Corporation Private Limited that, when executed, sideloaded a rogue DLL (“ffmpeg.dll”) codenamed Krita Loader.
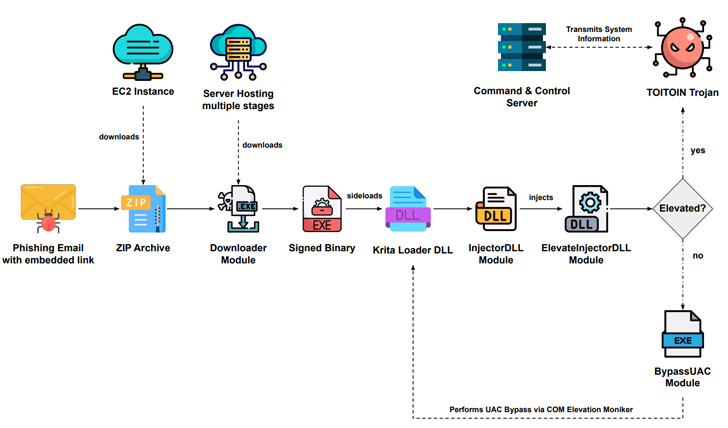
On the other hand, the loader is designed to decode the downloaded JPG file with other payloads and launch another executable known as the InjectorDLL module, which reverses the second JPG file, called the ElevateInjectorDLL module.
The InjectorDLL component then proceeds to inject ElevateInjectorDLL into the “explorer.exe” process, which then bypasses User Account Control (UAC), if necessary, to elevate process privileges and decrypt the TOITOIN Trojan, and is injected into the “.svchost.exe” process.
“This technique allows malware to manipulate system files and execute commands with elevated privileges, thereby facilitating further malicious activities,” the researchers explained.
TOITOIN comes with system information as well as capabilities to collect data from installed web browsers such as Google Chrome, Microsoft Edge and Internet Explorer, Mozilla Firefox and Opera. In addition, it checks the presence of Topaz Online Fraud Detection (OFD), an anti-fraud module integrated into banking platforms in the LATAM region.
The nature of the responses from the command-and-control (C2) server is currently not known as the server is no longer available.
“Through deceptive phishing emails, complex redirect mechanisms and domain diversification, threat actors successfully distribute their malicious payloads,” the researchers said. “The multi-stage infection chain observed in this campaign involved the use of custom-developed modules that employed various evasion techniques and encryption methods.”
