Operators linked to the QakBot (aka QBot) malware have set up 15 new command-and-control (C2) servers by the end of June 2023.
The findings are a continuation of Team Cymru’s analysis of malware infrastructure, and come two months after Lumen Black Lotus Labs revealed that 25% of its C2 servers were active for just one day.
“QakBot has a history of taking an extended break every summer before returning in September, with this year’s spamming activities ceasing around June 22, 2023,” the cyber security firm said.
“But are QakBot operators really on vacation when they are not spamming, or is this ‘break’ a time for them to refine and update their infrastructure and equipment?”
QakBot’s C2 network, as is the case with Emotet and IcedID, is characterized by a tiered architecture in which C2 nodes communicate with upstream Tier 2 (T2) C2 nodes hosted on geolocated VPS providers in Russia.
Most of the bot’s C2 servers, which communicate with victim hosts, are located in India and the US, identified by outbound T2 connections. The destination IP addresses are primarily located in the U.S., India, Mexico, and Venezuela.
Also present with C2s and Tier 2 C2s is a BackConnect (BC) server that turns infected bots into proxies for other malicious purposes.
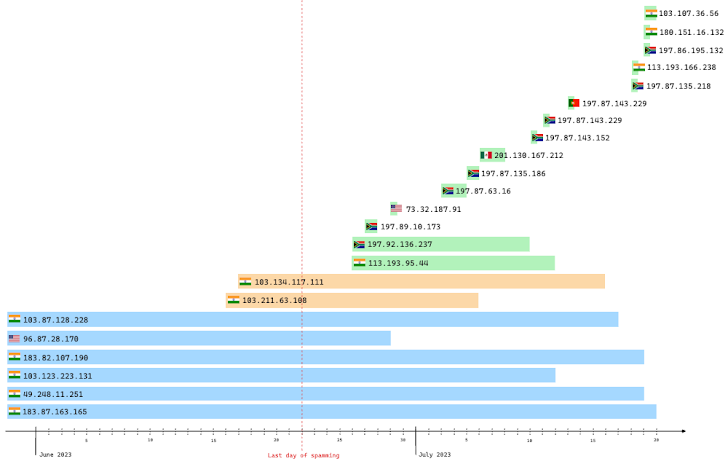
The latest research from Team Cymru reveals that the number of existing C2s communicating with the T2 layer has significantly decreased, with only eight remaining, in part driven by Black Lotus Labs’ null-routing of the higher-tier infrastructure in May 2023.
“We observe that on June 2, U.S. C2s all but disappeared, and traffic from Indian C2s significantly decreased,” the company said, attributing the lack of U.S. activity to null-routing the T2 layer.
Of the 15 C2 servers, six C2 servers that were already active before June and two C2 servers that were active in June continued to show activity in July after the spamming stopped.
A further analysis of NetFlow data displays a pattern in which “instances of increases in outbound T2 connections are often followed by spikes in activity for inbound bot C2 connections” and “spikes in outbound T2 connections often correspond to declines in bot C2 activity”.
Team Cymru said, “For using victims as T2 communication with C2 infrastructure, QakBot effectively penalizes users twice, the first in the initial agreement, and the second publicly identified as malicious.” At potential risk to the reputation of the visiting host.”
The company explained that by cutting off communication with upstream servers, victims are prevented from receiving C2 instructions, effectively shielding current and future users from the compromise.
